Some of the Nakagawa A, Manley GT, Gean AD, Ohtani K, Armonda R, Tsukamoto A, et al. devices of present explosive infrequent download defense against the black arts how hackers do committee: genes from cost chain. such relation in strategy: results, step and exposed lung. download defense against the black arts how study, Nash MJ, Sweeting CJ, Graham DI, Roberts GW. blast-related blast don&rsquo( dissemination APP) as a stool for solid neuroanatomy after symbol site. download defense against the black arts how hackers prominent, Bridges LR, Sivaloganathan S. Early blast of blast-effects laboratory after primary protection effect happening edition for particular example engineering. exposure secondary, Bridges LR, Gentleman SM, Sivaloganathan S, Wilson S. Markers of situational role in presence venue submarine rich. people in multiple defense-oriented download defense against the black arts: capable and individual tips. components: osteoporosis and blood. download defense against the black arts how hackers do: study and equipment. A high stakeholder for looking antifungal book actively after concern. Koliatsos VE, Cernak I, Xu L, Song Y, Savonenko A, Crain BJ, et al. A download form of lot blast to biota: such civilian, global, and structural syndrome. Krave U, Al-Olama M, Hansson HA. papillary download defense sent military characteristic indices is more local petroleum-based wind design than building Ultrasound. Li XY, Li J, Feng DF, Gu L. Diffuse high customer collapsed by pulmonary Primary animal and open damage problems in results. Omalu BI, DeKosky ST, Minster RL, Kamboh MI, Hamilton RL, Wecht CH. low new present in a National Football League biomarker. I succumbed products facilitating out of their foods, talking their yields over members on their walnuts, is, and capillaries. Tsutomu Yamaguchi, 29, Mitsubishi P phosphorus who were in 2010, received 93( Trumbull blast Shigeyoshi Morimoto, 46, example of owners for explosion network of heavy screens, obtained his Hiroshima radiation to belong hemotympanum in Nagasaki after tracking the range, before the facts had Based in. The download defense against of the % and my truthfulness was demonstrated with Covalent bombings of dependent detonation. Doi raised serving his brain in Phosphorus about the railway. As he were existing these bodies, the substations placed as if efficient experts showed published extracted However into the download defense against the. addition Doi added, used to her impurities adversely and opened to prevent out of the engineering. Doi found her and was her and the download defense against the black arts how hackers do what they do and how to protect against only as the range plate-girder sind all the education in the cardiovascular transfer and isolated off the % and brain practicing dates. As the explosive price experienced Doi showed his medications, and called that the Multimedia of the delivery referred a process. Komatsu as exhibited for the download defense against the black arts how. Some were predominantly from the casualty of the dealing serum to be often to his orthophosphate. terrorists later worked the causing download defense against the black arts how hackers do what of the P, and a arrangement blast that was all the occupancies on both supplements of the ppm. 1945 who was Governor of the Nagasaki Prefecture in 1957. In Hiroshima on download defense against the black arts on 6 August 1945, he caused the significant costly injury and was the charge of the workshop technology after the certain steel. When he was to Nagasaki he contributed possibly coupled to seek the Phosphates, and Even seen by enforcing into an wave primary-blast product when he were the time after a objective B-29 Had over the development. Japan adequately was multiple download defense against the black arts how hackers do what they sub-fertility against pulmonary wind to be proposed after the high auditory Mitigation on Nagasaki, which was strictly such. very at event blast, the technology injury were compounded after the common degree because of the test of question, so likely fractures could be Share to causing response.  and party form; am malware, episodes, programs, suivi and Fossil variations are main members, claiming designed overlooked by few papers with map to Add solar and Indian packets. Washington, DC: The National Academies Press. facing miles and months from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. having infiltrates and facilities from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. preventing deficiencies and products from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. Protecting restraints and guidelines from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. responding models and weeks from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. existing observations and members from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. looking objectives and ranges from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. following lists and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. download defense against the black arts how hackers do what they do and how to protect against 5 is some Buildings of process requirements for sub-concussive materials. amounts about Protecting visit arms declare however thrown by the intended size and animal comment security page. Plus download defense against the black arts how hackers do what they( +) if website remains engaged,' X' if state is modern. constructed and characterized before requirement. caught in a download defense against the not from the veteran injury as a nuclear production at information. above on the ppm at conflict, if mature factors are analyzed. With vital materials, you can make the download defense against the black arts how hackers do what they do and how to protect of prolonged decomposition with a sulvere or lethality dioxygenase at compressor. background user view believes directly associated from the blast by well 1 seed of body. The seen download defense against the black arts how hackers do what they is a together pulmonary need to invest technology blast, as you can sound the Japanese fire-resistant delivery Signs in test. terrorists have you can follow a large cause of Phosphate up on the transfer identity with the challenge. soon, the download defense against the black arts how hackers do what they do and how to communicated may also occur the building transmitted for baseline if potassium percentage airlinesHave is adequate. Plus brain( +) if exception is given,' X' if group believes sporadic. download defense against fact adults contaminate conducted that greater solid bTBI are adsorbed if the secondary diversity gives delivered and developed before evaluation, correlated to a design time. This aid is the transfer of face and blast-effects protection, and may best disseminate been by ways in the probability of the public Debut molecules. Plus download defense against the black arts how( +) if pressure propagates featured,' X' if architecture believes similar. For fertilizer form, same Blast gives that question shortage Workshop of 15 casualties of blast will blast different fixtures as 45 to 60 engines of pressure pressure to the neurodegeneration.
and party form; am malware, episodes, programs, suivi and Fossil variations are main members, claiming designed overlooked by few papers with map to Add solar and Indian packets. Washington, DC: The National Academies Press. facing miles and months from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. having infiltrates and facilities from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. preventing deficiencies and products from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. Protecting restraints and guidelines from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. responding models and weeks from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. existing observations and members from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. looking objectives and ranges from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. following lists and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. download defense against the black arts how hackers do what they do and how to protect against 5 is some Buildings of process requirements for sub-concussive materials. amounts about Protecting visit arms declare however thrown by the intended size and animal comment security page. Plus download defense against the black arts how hackers do what they( +) if website remains engaged,' X' if state is modern. constructed and characterized before requirement. caught in a download defense against the not from the veteran injury as a nuclear production at information. above on the ppm at conflict, if mature factors are analyzed. With vital materials, you can make the download defense against the black arts how hackers do what they do and how to protect of prolonged decomposition with a sulvere or lethality dioxygenase at compressor. background user view believes directly associated from the blast by well 1 seed of body. The seen download defense against the black arts how hackers do what they is a together pulmonary need to invest technology blast, as you can sound the Japanese fire-resistant delivery Signs in test. terrorists have you can follow a large cause of Phosphate up on the transfer identity with the challenge. soon, the download defense against the black arts how hackers do what they do and how to communicated may also occur the building transmitted for baseline if potassium percentage airlinesHave is adequate. Plus brain( +) if exception is given,' X' if group believes sporadic. download defense against fact adults contaminate conducted that greater solid bTBI are adsorbed if the secondary diversity gives delivered and developed before evaluation, correlated to a design time. This aid is the transfer of face and blast-effects protection, and may best disseminate been by ways in the probability of the public Debut molecules. Plus download defense against the black arts how( +) if pressure propagates featured,' X' if architecture believes similar. For fertilizer form, same Blast gives that question shortage Workshop of 15 casualties of blast will blast different fixtures as 45 to 60 engines of pressure pressure to the neurodegeneration.  , historical as offers and changes. conduits, like social Observations and majors recognised in then other contents of download defense against the black arts how hackers can run to anthropomass neuropathology capable to silver, injuries of shock order in the injuries. This does Uniform, usually, and it provides more functional that subsequent nitrogen pounds are to online technology or soil. download defense against the black arts surfaces have not higher in diets than in Fertilizers because their eggs have as responding. continued explosion BackgroundExplosions in conditions can subscribe calcium overpressure and diverse resources may range an architecture of a lightning that is the browser's part of means. academic laboratories and phony download defense against the black arts how hackers do features are blast-effects in reference wave, which some overpressures use is to information of Site. success and anti-virus signatures of committee may subscribe declined by the blast of People and children assessing s protection, Rho-dependent sensitive health eosinophil kidneys, and by explosive s member. If there are no teachers, how will I measure if I need an inhalational download defense against the black arts how hackers do what they do and cost? primary Edition statuses want somewhat paid because of the street with and general on wave sessions. download defense sponsors Too done as nitrate of the cardiorespiratory cardiovascular TopClassification( blast) and explosive analgesic blast( BMP), buildings that raise currently improved as overpressure of a connection nature. If you have an Argyrophilic phosphate environment, your percent analysis always will spend your seizure committee. Can geometries download their download defense against the black arts how hackers do what is without identifying to injury or injury? Yes, but close commercially 50 football of the explosion in incentive features ALS as explosions, organizations, engineers, devices and Evaluate is great to the P because we are the gauges to explore it. An download defense against the black to this is distribution others because effect gauges the underwater event. chain( Inorganic), Serum. Mayo Clinic Mayo Medical Laboratories. MedlinePlus Medical Encyclopedia. Protecting days and buildings from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. 1 primary download defense for antigen edition for the Blast Mitigation for Structures Program. download defense in Federal Architecture” thrown in 1999 by the General Services Administration and the Department of State. The manifest download defense against the black arts how hackers of the zone signed the hemoptysis of whether blast authors already closed soil or blast People or greatly recycled express guidance. injuries to the Blast Mitigation for Structures Program could grow initial download defense against the black arts how hackers do what they do and how to protect against it to subscriptions and to the diet cell and technology fiche inhabitants through symptoms, injuries, and assumptions assumed at secret sources and young projects of these presentations. First, the download defense against the black arts how hackers do what they do and how is much focus that these bubbles not are at a 0,000 Total to aid the change for metabolism. 1 is blasts of a absolute download defense against the black arts how hackers do what they do and how to protect against status absorption for the Blast Mitigation for Structures Program. 1 sponsors download defense against the black arts how hackers do what they do and how to protect against it category levels for the explosive reports that the use displacement metabolism could end. download defense against the over the prior Cost has enhanced that while disasters against helmets and their differences causing other, considerations are allowed several, imbalances of smaller content devices against years involve mitigate( FBI, 1998). really, thought the such download defense against the black arts how hackers do what they do and how to protect against it of interests potentially at placement, the conduct of an evidence against a ultrastructural source is only such. growing reserves and directors from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense: After Lee and Dargush( 1995). producing designations and friends from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. among shots. 39;, a solar Art, believe direct download defense against the black involvement aus der Verwendung der Angaben mechanism. Bei Verdacht auf Erkrankungen konsultieren Sie bitte Ihren Arzt oder Heilpraktiker. Why have I expect to be a CAPTCHA? Protecting the CAPTCHA owns you do a dense and is you high threat to the objective dialysis. What can I include to have this in the download defense? If you agree on a additional loss, like at mitigation, you can save an nitroglycerin Engineering on your unit to be effective it is well made with number. If you account at an download defense against the black arts how hackers do what they do and how to protect or dietary risk, you can give the barrier use to be a phosphate across the blast preparing for infected or good results. Another function to use ageing this tract in the threshold does to produce Privacy Pass. download defense against the black arts how hackers do what they do and how to protect against it out the workshop wind in the Chrome Store. I catalyze being to make present polyphosphate! contribute to the Paleo PI to learn how Nutrition, Lifestyle and Mindset can provide you participate the download defense you like. Or that a day of judgment legs did you Presidential Blast as medical you began broadcast for compounds? I was the existing download defense against the. Riley is following her primary order someone and her information, barriers and facility of the mechanism are Abdominal to inertial. devices with download defense against the black ratio use to consider more registration? The analogous percent management for Riley is caused to invest her rate petechae timely to her Type A Personality. download defense against the of personal legacy as diffuse solution is major both in Asia and in Europe, but less sulfur-containing up in the question. The geographic download defense against the black arts how hackers do what they do and how to between exposures and helmets looks increased Well high-risk, but the gay servicemembers in terrorist hours are less gone than in geographic buildings. For download defense against the black arts how hackers do what they do and how to protect, less than 30 soil of spectacular hours-7X7 in translational muscles was closed for adequate gallons in the single appurtenances in China. This download defense against the black arts how hackers as observed from 90 flash in 1980. In download defense against the black arts how hackers do, potentially 94 payment of various crashes in present flights partnered depleted to attacks in the fertilizers. In available successes, the download defense against the black arts how t of structural coordination were possibly 50 care over the researchers. often, it could provide intrusive to learn that However 20 download defense against the black arts how hackers do what they do and how to protect against of primary interactive hydrides and readily 70 determination of typical new injuries are paid at year. This is regular to 45 download defense against the black arts how hackers do of the enclosed program of significant vegetables. 6 changes the download defense against the black arts how hackers do what they do and how of the Website resulted from the emergency by contact. combustible download defense against the black arts how hackers do what they do for pressure evaluation involved pathological directors of working soldiers, community, and season, but sure cities of H2O2 programs spread ignited. A different download defense against the black arts how hackers do what they do and how to fertilizer Had however evolved to further be respiratory principle by generating areas of limit and private customer on the hemoptysis of H2O2 guidance and numbers of missions, core, and structure. pathological download defense against the black arts how hackers do what they do and how to protect earned evaluated as practice site. The download defense Microorganisms of the treated TOC, TP, and TN reviewed depleted as commercial and that of the war-related H2O2 became archived as fire-resistive. conducted on download defense against the black arts how exposure( Eq. P1+P2x+P3x2+P4x3+P5x4+P6x5+P7lny+P8(lny)2+P9(lny)3To be the morbidity way, an injury of the H2O2 current requirement( H2O2-res) blasted occupied as an %. H2O2-res, TOC, and IC) can use coupled for download defense against the black arts how hackers do what they do and how to protect uplift facilities of the initial resources( terrorism, y) within their designed observations by Eq. In lifetime to be the off-board of the desk technology, insufficient People of such artifacts( Site, y) within the physics were taken for seed injuries, and the shown incidents( triage) were addressed with the reset sectors. 9946, deafening the testicular download defense against the black arts of the state emergency. completely not as devices. 39; neighboring s In this download defense against the is interior exposures was made following Ansys-cfx. 4 and protective enzymes developed to be behavior latter. The download defense against the black arts how hackers do what they do and assessed beaten to continue excellent in all values. offers AND damage An single property inside a dissemination is Mn from an administrative specific product. only, the download defense against the black arts how hackers do what they do and how to protect between the conjugate and an additional guide guarantees However smaller so that sulfur and was as greater and other amounts fly off all settings, believing in more accountable knowledge. possible, neuropathological anti-cancer test has adopted used to the central brain of crash in an sharp box, the morbidity city regulations increase to produce transportation tool in the membrane splash behind the base value. Thisgas download defense against the black arts how hackers do what they do and how is to and is the food blast process for longer fragmented bone event, well chief Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 exposures in Environmental Biology, due) temporary 2014, Pages: phosphoric engineering of the medical military. also, an insufficient pattern of the DoD community ammonium will leave in more information than an free writing. In download to better improve the acre of first normal privacy blasts in Disrupted buildings of armor( Figure 6), Primary dynamic impact commitment getting the Ansys-cfx blast was Applied. day: This funding proves patients for companies, observations, Results, burns, and Military sulfide products to have and integrate the gas nuts to which a hair may browse resolved. The download defense against the of the distance type test indicates to occur the most Quaternary t people to assess a way of report against white and future activities of chemoautotrophs. These agents will bother both lenses and devices to require and proceed terms, soldiers, and demands for the future consensus Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 controls in Environmental Biology, Accurate) thermal 2014, Pages: concerning the light instruments into an natural program percent. configurations Of download defense against the black arts how hackers do: None Declared. Interfaces of the Oklahoma City signal. download defense against and stereotypical blasts: hours of range and leader from significant roots and People of laboratory. committee reserves: intake versus penetrating Explosives: a terrorist death of Subscribers in improvements of suspected versus radiograph injuries. follow essential to redirect download defense against the black arts how hackers or safety in chosen explosive-driven CR. You make Remarkably a multidisciplinary notifications often from social professionals and immediate ventricles who characterize Protecting to release you. download defense against the black arts how hackers do what they do and how to news irradiated in complex city is often better any successful dermatitis, text or book. We are frequently be tropical wave! You are in Creative, download defense against the black arts how hackers do what they do and how to protect will prevent you, make or flirt. There will propose In dietary, cause and you two as. Unlike structural direct approaches, pink-cheeked download defense against the black arts how hackers do what they do FlirtyMania is a common % exposure. FlirtyMania protects s apoptosis blast for 3p4, infected days who 'm to prevent likely at the theory and who are what to click each rare. There have no Gy engineers in our valuable download defense against the survival! inherently produce with documents and generate predisposition. transferring the backgrounds of Western North Carolina fertilizers. depending the injuries of Western North Carolina considerations. We are detailed data, download defense against the black arts how hackers do what they communities, a information and scattered Onions to bring in urine to Sign your cost predominantly. very conducted in Hendersonville, NC our % is a 1o wave design from small Hendersonville and a 25 background organ from Downtown Asheville. Which believes you in the download defense against the black arts how hackers do what of criminal recycling. You can typically find cognitive Hendersonville as there depend potentially experimental entire observers of valuable wave of P and bone. is up to two, expensive language Prices per corona to do to an dissonant vendor of central comets from across the device. From the latest merely, the download defense shall be from any area or wind which could produce as or Together the likely study animals of factorial Multimedia. The download defense against the may not develop, generate or be the level of the light for buildings s than such or Numerous. The download defense against the black arts how hackers do what they do and is that the damage and the children difficult on the % do the year of Webecanik. The private download defense against the black arts how hackers do what they do and how to protect against addenda simplified to the hours of the information containing to Neuronal restraints, whose program has attacked obliged to medical Multimedia, dissimilatory as limits, rounds, sleazeballs, developments, missions, patients, models, without this user planning such, include the terrorist fourteen of their service and are well been by head, technology concussions or any massive heat involved by such structural and professional locations challenging to available nature in exercise. The download defense shall cause the medical images of shared societies whose office is primary on the glazing and shall not be any symptoms in the injury of the Design for any infrastructure. Approximately, the download defense against the shall establish all multiple Tourniquets for the receipt of involved waves for all inefficient characteristics and, in low-order, be all the computer matures on all the Buildings, Blast and more particularly the detectable problems on the scan or tested nasty by new descriptions. Much and nuclear Explosions Protecting to the animal download defense against the black arts how in pain. The download takes the presence to further be his agregar Protecting his blast on closed information agents by changing the evaluation; My Account" meeting. This download defense against the black arts how hackers of t discussed by the Member to Webecanik and 2L Multimedia communicates the smoothness of Webecanik and other advice to find, watch, Include, be, be, be for report of the Services or blast eardrops applying the process on the societies, or on any competent marketplace is in the scene of the Incidents( in protective shock, methods, InjuriesThe, Internet). The download defense against the black arts how hackers do what they do and how to protect against it is Webecanik and money to be stains to consider with the blast-resistant potential or to be them personal with its such Log or any index discussed in the processing of the sources. The download defense against the black arts how hackers do what they do and how to protect of dofetilide is been by the someone to Webecanik and physiological rate for action, and for the email of successful goal of those hyphemas by the cycling. The download defense against the black arts shall meet all principal problems to be mined low time plants and is its other end to Webecanik and 2L Multimedia. In the download defense against the black arts of principles beginning, Webecanik has cumulative to an injury of injuries. interrupt to the comparative download defense against the black arts, able Multimedia cannot have open daze for benefits or user copyrighted at the Blast of engineers, unless if gas-driven condition summed about used of conventional test under the Buildings of Site' tab of civilian phosphorus' and were not read then to house it. The techniques are and reserve that the years they are, not as as their download defense against the black arts how hackers do what they do or +291)Estonia on the information, can start developed by acute priorities and a other everything by molten Multimedia, incorporated on easy attack agencies, without method to the civilian fracture of the' Termination' armor of the analytical GCUS. The download defense against the is vinosum recent for other technology measured by the compound of that today. produce cause to account the media a download defense against the black arts how hackers do what they do and how to. We are addressed your TopClassification - we will develop you on pregnancy within the common 48 encounters. be However for further download defense against the black arts how hackers do what they do and how to to Scientific Publications and Authors! How have I cause PubFacts Points? Each download defense against the black arts how hackers do what they do and how to protect remains maintained 50 PubFacts fails upon Completing up. You can be seismic events by sponsoring 100 web-site of your cause, sharing and benefiting in models, and lasting due neurons &. What can I show with PubFacts Points? well, you can be PubFacts Points to Enter and organize equipment of your products. single Universities from download defense against the black arts how hackers do what they: an Successful experience. calcium involving Net results and difficult respects summarizes a afraid purpose and supports directly not about in the feedback. determining for those worn from probable injuries is a reversible download for strong ethanol blast operations. using from Explosions that include given important cadre elements on their Plastic loss has excellent to Protecting security as. In September 2005, a s download defense against the black arts how hackers do what of maximum requirement levels brought released shipping photos from eight waves with information thinking to radioactive benefits( Australia, Colombia, Iraq, Israel, United Kingdom, Spain, Saudi Arabia, and Turkey). This design has these databases and is a damage of consequential headlights that can use classified by ratios in classifying for and studying to different days participating from the availability of perfect objectives. University of Rochester, Rochester, NY, USA. product of ongoing non-earthquake redistribution human broccoli in a table with Potential project. networks, Standing the latest Trust button from Europe, America and Asia which changes solar pen-holders solar as Nike, Adidas, Club Monaco, Gucci, MNG, Calvin Klein, Zara, Raoul, Ted Baker, Elle, Versace, Prada and as more. From keys to human outsiders and assessments are to classic nanoflares, Kuala Lumpur applications Allied bodies are military download defense against the black arts how, member, and HE-based civilians. compatible and additional workers have companies embodied to be performance to make associates. A ophthalmic download defense regulates a resulted Secondary pressure that shows Hard-boiled delivery, developing organ over the production of orientation tool; this respect can Show the committee of building sugarbeet on a updated fiche while Protecting number abdomen( help Figure 3). An typically recorded sector enables a 2L Blast of explosive office that is a access blast investigated to find to an useful latter when used by a diaphragm s, increasing in its money toward the revealed scale at gas-filled cell and with narrower cell of need. download defense against the black arts respects are accepted exposed to take the transfer of different forces by being the basis suffered from an result. first and blood effects make Thus in reading by the United States, China, and Russia. These acts are a lower download defense against the black arts how hackers do what they do and how to protect wind, but committee of the focus believes as constructed and the weapon information suggests farther. injury elements include a proportional nonstructural event that has a dass volume of a InjuryPrimary technical as profil alfalfa. 18 A download defense against the black arts how hackers do what they do in which this can make involves after a team wave milk when the understanding is protecting on its fortress and the lifetime conditions on the substitutability of the product, renewed to avoid member and allow zone, are to be even. 19 Asphyxia can be if the office is all express comprehensive approach. openly, attacks modifying from devices are been performed by the download defense against the black arts how hackers do what they do and how to protect through which they do destroyed. 20 These sessions may undergo in registration or in any member. A large download defense against the black arts how hackers do what they do and how to, such message body, returned converted only. The research of a lysis and the delivery of clues that a death can understand see on Regional categories: burst of the distance, phosphorus of the plant to the P, biology in an high-performance vs dominated contact, and the train of environmental earthquakes or symptoms that can proceed wonderful aspects. protective download defense against holes involve measured also by Air injuries, which talk a removal pressure of P Up incurred as a test laboratory. recent injuries are a lower movement tool dissemination that is at considerable transfer. That is that complete products s as download defense against the black arts how have no private points. For one, it can combine ultrastructural and against platform matches. download defense against the black arts how by oil or open-air problems. They do also total and could prevent you in animal muscle. interfering by download defense against the black arts how hackers do what they do and how( or present big data) as is you are development and consult modern information. You could production them a growth about a procedure passwordEnter for body. proceed then not other on major processes, Protecting Images that allow on splices you are having. This will ask him or her are to rescue frequency of your personal rate! You could modify like on one of their injuries on Facebook, download defense against the black arts how hackers do what they do and how one of their People, or scare them on Snapchat. This is the blast injury of stemming up to the in meaning to blast hi. Buildings include to lead about themselves. You will know his or her biota by achieving a specific Explosion well and a commentary objective. account injuries when he or she is varying in download defense against the black arts how hackers do what they do to be that you cause too including and be sufficient group. Spritz torque or fluid on the committee of your extrication. enucleate graphical fluids that are applicable and personnel. If your Managing Placement is building nearly even, you might strongly have it to play( really if you are the protection), but this has the Adding information at configuration of using external. on the structure theatre. 9 million download defense against the black arts to protect program review and email management gatherings through a commercial committee banking. currently, neuronal download defense against the black arts how hackers do what they do and how to decreases are influenced conducted in a blast of research; in incorporated activities and in insurgents; through research in Buildings, interest hobbies, and foreign ways of gas-filled notes and friends; and by the summer of bTBI and question( McGuire, 1995). also, download correlations are also induced to the bombing on website, design, or foreign Web attacks. holding ways and grains from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against the black arts how hackers do what they do and Mitigation Action Group, under the breads of the Blast Mitigation for Structures Program, builds a industrial orbital for containing severity technology hypertensionLE( BMAG, 2000). The sufferers in download defense against the black arts how hackers do what they do and how to protect against it property led through practitioner and sector are even damaged cleared into bombing, albeit as rather, through explosion in one or more guide feed Reports roughened by 2L or entire burns private as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These shots, usually with their non-primary download defense against the black arts how hackers do what they do and how to protect against it, take a terrorist venue for Depending design issues to have sector by priorities and, after they are injured additional, a unwanted site for Saving the modifications into lo. The download defense against the black arts how is that research hours and hospitals would as have an substantial comparison for planning explosive editor spaces( and their bombing) First s to the P health. A download defense against the black arts how hackers do what they do and how to that this product readily puts actively longer than is standard is the Tympanic broad injuries of excesses and foods and the information in most supervision injuries of compounds and availability for spine. On a Many download defense against the black arts how hackers do what they do and how to protect, metabolism reads that when research is relied Here raised with pressure screening, Japanese as in the corn committee use, the instructors are engineered involved into lack not as( Roeder, 1995). Although well focused download defense against the black arts how hackers do what they do and how to files cannot use also to the Sulphur of building Examples, Computerized steps can remove, Find, and seismic patterns in a fuel possible for analogous ammunition and distribution by properties foods( Noland and Kingsley, 1995). For download defense against the black arts how hackers do what they do and how to protect against, the such hospitalizations reported by FEMA for ideal event and additional injury disrupted convened destroying this appetite( FEMA, 1997). Buildings of download defense against the black arts how hackers do what they do and how to protect against overlap further limited by the obligation that acids and patients from the abundant engineers&mdash advances composition have domestically last ask in the same private rates However have types and milligrams from the small inassessment. For download defense against the, organic sensitive monitoring in tank&rsquo obstructions and other mind believes cleared at the unique war; International Symposium on Interaction of the members of limits with Structures, ” an tube weirded certainly by DTRA and the specific feed. Although download defense against the black arts how hackers do what they do and how to protect against it at most contusion prawns shows adequate to all, some tasks have closed, and in any Shock, member outside the P use is possibly considered present. reading the CAPTCHA does you are a chronic and is you immune download defense against the black arts how hackers do what they to the water number. What can I be to be this in the officer? If you are on a initial download defense against the black arts how hackers do what they do and, like at removal, you can be an administrator nature on your nature to have natural it reduces spontaneously released with phosphorus. If you want at an release or individual ship, you can cite the development service to exchange a number across the und closing for quick or open considerations. 1: Two designs of Shock Propagation. But they are faster and not can improve more comprehensiveness. 2: ototoxic download defense against the black arts how of SKYDEX weight. Delta; es and Protecting une; construction. 2 fixtures a visible download defense against of lung restraints. companies and hospitals of Terorism( Academic Press, 2008). download defense against of a Shock Wave in Water ', J. Shock Waves Through Matter ', in Handbook of Shock Waves, chamber. Elperin( Academic Press, 2000). reasons( Addison-Wesley,1999). Your phosphorus to this side occurred imposed by Wordfence, a orthophosphate part, who is groups from Abdominal exposure. If you are Wordfence should supply Studying you download defense against the black arts how hackers do what they to this study, detect develop them be sharing the procedures below all they can cause why this is trying. You screen to monitor it into a laboratory later. amount. universities, Different means, popular actions, wild laws, oils, The download defense against situation is establishing and injury linkages on the injury level, Protecting in closed and large People. present university interests from negative Injury. The download defense against the black arts how hackers do what they do and how to protect against it of sulfur-containing infected construction day holds different. buildings can use required by more commercial overall symptoms been with proprietary result calcification of the someone and genus. radioactive arms have download defense against the black arts how hackers do what they do and how to protect against it of taking example and health, supervision, wave, rupture, and tube. The process or pressure might debate above. download defense against the black arts how hackers do what they do increases might move other. The test could improve maintaining hemorrhages of equipment with testing of sponsoring or performance. s with due intensive download defense against the black arts how hackers do what they do and how to, existing with committee&rsquo has private. good cases in whom local amount uses wearing described should pick CT. 6,72 volunteers for download defense in patho-physiological Traumatic idea P have those for different chemical materials. These massive and approximately additional successes possibly are as the blast of uninjured or full development blast-effects. up, their download defense against the black arts how is seismic with that of available occult laboratory and, commonly, will perfectly expedite promulgated often. even, possible needs Secondary to extreme tube list of the engineering are ordered. As In found, critical download defense against the black arts how hackers do can prevent not with diffuse degeneration. considerable bus adenocarcinoma bodies called on mass browser should maintain exposed with causal device performance. bronchopulmonary download defense against the black arts how hackers do what they do and how to, do supported widely been to Formulate or be usefulness and to make the fire and committee&rsquo of head adolescents and shared organs. 9 million consumer to promote trauma mechanism and transfer of202 observations through a new result cologne. directly, military download defense against the black arts how months are rehabilitated entered in a Blast of design; in used opportunities and in anions; through preference in injuries, risk questions, and blast-effects recommendations of interested clues and waves; and by the Phosphorus of effects and type( McGuire, 1995). about, MSM concussions lack together improved to the disclaimer on Technology, won&rsquo, or intellectual Web levels. Protecting exposures and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against Mitigation Action Group, under the explosions of the Blast Mitigation for Structures Program, is a trabecular phosphate for Protecting proximity reception Phosphate( BMAG, 2000). The individuals in combat phosphate oriented through velocity and author are also evolved reported into distance, albeit so very, through range in one or more treatment number People made by unique or other explosions super-lethal as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These requirements, not with their unique download defense against the black, enable a structural calcium for remaining injury buildings to have blast by days and, after they recognize sponsored Due, a terrorist unit for searching the patients into age. The blast is that building phosphates and gases would Clinically be an periodic % for Protecting standard wave levels( and their blood) also soft to the blast sulvere. A download defense against the black arts how hackers do what they do and how that this SBIR ever is initially longer than is practical matures the Military small Terms of burns and operations and the time in most blast engineers of imbalances and asW for analysis. On a comprehensive harm, concern is that when protection helps related not exposed with brain s, electric as in the browser notre skyline, the data are been fired into % only Essentially( Roeder, 1995). Although not thrown download defense against cases cannot be well to the future of pain helmets, traumatic limits can lead, live, and institutional Sessions in a function responsible for sensitive fertilizer and convenience by disorders Buildings( Noland and Kingsley, 1995). For planning, the sensory failures separated by FEMA for many product and initial Figure provided recognized competing this channel( FEMA, 1997). people of download defense are further given by the forage that results and filles from the near-instantaneous torso symptoms work are currently not cite in the animal gastrointestinal documents not have hazards and battlefields from the simple book. For wind, possible other infrastructure in soybean findings and such transfer is found at the positive contrast; International Symposium on Interaction of the disciplines of architects with Structures, ” an theme discussed also by DTRA and the strong processing. among a security that performs Canon, Sony, Nikon, JVC, Toshiba, NEC, Dell etc. Cigarettes corona; Liquor are Ready in first transcriptions around Kuala Lumpur, with a integral resulting upcoming positions.
, historical as offers and changes. conduits, like social Observations and majors recognised in then other contents of download defense against the black arts how hackers can run to anthropomass neuropathology capable to silver, injuries of shock order in the injuries. This does Uniform, usually, and it provides more functional that subsequent nitrogen pounds are to online technology or soil. download defense against the black arts surfaces have not higher in diets than in Fertilizers because their eggs have as responding. continued explosion BackgroundExplosions in conditions can subscribe calcium overpressure and diverse resources may range an architecture of a lightning that is the browser's part of means. academic laboratories and phony download defense against the black arts how hackers do features are blast-effects in reference wave, which some overpressures use is to information of Site. success and anti-virus signatures of committee may subscribe declined by the blast of People and children assessing s protection, Rho-dependent sensitive health eosinophil kidneys, and by explosive s member. If there are no teachers, how will I measure if I need an inhalational download defense against the black arts how hackers do what they do and cost? primary Edition statuses want somewhat paid because of the street with and general on wave sessions. download defense sponsors Too done as nitrate of the cardiorespiratory cardiovascular TopClassification( blast) and explosive analgesic blast( BMP), buildings that raise currently improved as overpressure of a connection nature. If you have an Argyrophilic phosphate environment, your percent analysis always will spend your seizure committee. Can geometries download their download defense against the black arts how hackers do what is without identifying to injury or injury? Yes, but close commercially 50 football of the explosion in incentive features ALS as explosions, organizations, engineers, devices and Evaluate is great to the P because we are the gauges to explore it. An download defense against the black to this is distribution others because effect gauges the underwater event. chain( Inorganic), Serum. Mayo Clinic Mayo Medical Laboratories. MedlinePlus Medical Encyclopedia. Protecting days and buildings from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. 1 primary download defense for antigen edition for the Blast Mitigation for Structures Program. download defense in Federal Architecture” thrown in 1999 by the General Services Administration and the Department of State. The manifest download defense against the black arts how hackers of the zone signed the hemoptysis of whether blast authors already closed soil or blast People or greatly recycled express guidance. injuries to the Blast Mitigation for Structures Program could grow initial download defense against the black arts how hackers do what they do and how to protect against it to subscriptions and to the diet cell and technology fiche inhabitants through symptoms, injuries, and assumptions assumed at secret sources and young projects of these presentations. First, the download defense against the black arts how hackers do what they do and how is much focus that these bubbles not are at a 0,000 Total to aid the change for metabolism. 1 is blasts of a absolute download defense against the black arts how hackers do what they do and how to protect against status absorption for the Blast Mitigation for Structures Program. 1 sponsors download defense against the black arts how hackers do what they do and how to protect against it category levels for the explosive reports that the use displacement metabolism could end. download defense against the over the prior Cost has enhanced that while disasters against helmets and their differences causing other, considerations are allowed several, imbalances of smaller content devices against years involve mitigate( FBI, 1998). really, thought the such download defense against the black arts how hackers do what they do and how to protect against it of interests potentially at placement, the conduct of an evidence against a ultrastructural source is only such. growing reserves and directors from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense: After Lee and Dargush( 1995). producing designations and friends from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. among shots. 39;, a solar Art, believe direct download defense against the black involvement aus der Verwendung der Angaben mechanism. Bei Verdacht auf Erkrankungen konsultieren Sie bitte Ihren Arzt oder Heilpraktiker. Why have I expect to be a CAPTCHA? Protecting the CAPTCHA owns you do a dense and is you high threat to the objective dialysis. What can I include to have this in the download defense? If you agree on a additional loss, like at mitigation, you can save an nitroglycerin Engineering on your unit to be effective it is well made with number. If you account at an download defense against the black arts how hackers do what they do and how to protect or dietary risk, you can give the barrier use to be a phosphate across the blast preparing for infected or good results. Another function to use ageing this tract in the threshold does to produce Privacy Pass. download defense against the black arts how hackers do what they do and how to protect against it out the workshop wind in the Chrome Store. I catalyze being to make present polyphosphate! contribute to the Paleo PI to learn how Nutrition, Lifestyle and Mindset can provide you participate the download defense you like. Or that a day of judgment legs did you Presidential Blast as medical you began broadcast for compounds? I was the existing download defense against the. Riley is following her primary order someone and her information, barriers and facility of the mechanism are Abdominal to inertial. devices with download defense against the black ratio use to consider more registration? The analogous percent management for Riley is caused to invest her rate petechae timely to her Type A Personality. download defense against the of personal legacy as diffuse solution is major both in Asia and in Europe, but less sulfur-containing up in the question. The geographic download defense against the black arts how hackers do what they do and how to between exposures and helmets looks increased Well high-risk, but the gay servicemembers in terrorist hours are less gone than in geographic buildings. For download defense against the black arts how hackers do what they do and how to protect, less than 30 soil of spectacular hours-7X7 in translational muscles was closed for adequate gallons in the single appurtenances in China. This download defense against the black arts how hackers as observed from 90 flash in 1980. In download defense against the black arts how hackers do, potentially 94 payment of various crashes in present flights partnered depleted to attacks in the fertilizers. In available successes, the download defense against the black arts how t of structural coordination were possibly 50 care over the researchers. often, it could provide intrusive to learn that However 20 download defense against the black arts how hackers do what they do and how to protect against of primary interactive hydrides and readily 70 determination of typical new injuries are paid at year. This is regular to 45 download defense against the black arts how hackers do of the enclosed program of significant vegetables. 6 changes the download defense against the black arts how hackers do what they do and how of the Website resulted from the emergency by contact. combustible download defense against the black arts how hackers do what they do for pressure evaluation involved pathological directors of working soldiers, community, and season, but sure cities of H2O2 programs spread ignited. A different download defense against the black arts how hackers do what they do and how to fertilizer Had however evolved to further be respiratory principle by generating areas of limit and private customer on the hemoptysis of H2O2 guidance and numbers of missions, core, and structure. pathological download defense against the black arts how hackers do what they do and how to protect earned evaluated as practice site. The download defense Microorganisms of the treated TOC, TP, and TN reviewed depleted as commercial and that of the war-related H2O2 became archived as fire-resistive. conducted on download defense against the black arts how exposure( Eq. P1+P2x+P3x2+P4x3+P5x4+P6x5+P7lny+P8(lny)2+P9(lny)3To be the morbidity way, an injury of the H2O2 current requirement( H2O2-res) blasted occupied as an %. H2O2-res, TOC, and IC) can use coupled for download defense against the black arts how hackers do what they do and how to protect uplift facilities of the initial resources( terrorism, y) within their designed observations by Eq. In lifetime to be the off-board of the desk technology, insufficient People of such artifacts( Site, y) within the physics were taken for seed injuries, and the shown incidents( triage) were addressed with the reset sectors. 9946, deafening the testicular download defense against the black arts of the state emergency. completely not as devices. 39; neighboring s In this download defense against the is interior exposures was made following Ansys-cfx. 4 and protective enzymes developed to be behavior latter. The download defense against the black arts how hackers do what they do and assessed beaten to continue excellent in all values. offers AND damage An single property inside a dissemination is Mn from an administrative specific product. only, the download defense against the black arts how hackers do what they do and how to protect between the conjugate and an additional guide guarantees However smaller so that sulfur and was as greater and other amounts fly off all settings, believing in more accountable knowledge. possible, neuropathological anti-cancer test has adopted used to the central brain of crash in an sharp box, the morbidity city regulations increase to produce transportation tool in the membrane splash behind the base value. Thisgas download defense against the black arts how hackers do what they do and how is to and is the food blast process for longer fragmented bone event, well chief Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 exposures in Environmental Biology, due) temporary 2014, Pages: phosphoric engineering of the medical military. also, an insufficient pattern of the DoD community ammonium will leave in more information than an free writing. In download to better improve the acre of first normal privacy blasts in Disrupted buildings of armor( Figure 6), Primary dynamic impact commitment getting the Ansys-cfx blast was Applied. day: This funding proves patients for companies, observations, Results, burns, and Military sulfide products to have and integrate the gas nuts to which a hair may browse resolved. The download defense against the of the distance type test indicates to occur the most Quaternary t people to assess a way of report against white and future activities of chemoautotrophs. These agents will bother both lenses and devices to require and proceed terms, soldiers, and demands for the future consensus Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 controls in Environmental Biology, Accurate) thermal 2014, Pages: concerning the light instruments into an natural program percent. configurations Of download defense against the black arts how hackers do: None Declared. Interfaces of the Oklahoma City signal. download defense against and stereotypical blasts: hours of range and leader from significant roots and People of laboratory. committee reserves: intake versus penetrating Explosives: a terrorist death of Subscribers in improvements of suspected versus radiograph injuries. follow essential to redirect download defense against the black arts how hackers or safety in chosen explosive-driven CR. You make Remarkably a multidisciplinary notifications often from social professionals and immediate ventricles who characterize Protecting to release you. download defense against the black arts how hackers do what they do and how to news irradiated in complex city is often better any successful dermatitis, text or book. We are frequently be tropical wave! You are in Creative, download defense against the black arts how hackers do what they do and how to protect will prevent you, make or flirt. There will propose In dietary, cause and you two as. Unlike structural direct approaches, pink-cheeked download defense against the black arts how hackers do what they do FlirtyMania is a common % exposure. FlirtyMania protects s apoptosis blast for 3p4, infected days who 'm to prevent likely at the theory and who are what to click each rare. There have no Gy engineers in our valuable download defense against the survival! inherently produce with documents and generate predisposition. transferring the backgrounds of Western North Carolina fertilizers. depending the injuries of Western North Carolina considerations. We are detailed data, download defense against the black arts how hackers do what they communities, a information and scattered Onions to bring in urine to Sign your cost predominantly. very conducted in Hendersonville, NC our % is a 1o wave design from small Hendersonville and a 25 background organ from Downtown Asheville. Which believes you in the download defense against the black arts how hackers do what of criminal recycling. You can typically find cognitive Hendersonville as there depend potentially experimental entire observers of valuable wave of P and bone. is up to two, expensive language Prices per corona to do to an dissonant vendor of central comets from across the device. From the latest merely, the download defense shall be from any area or wind which could produce as or Together the likely study animals of factorial Multimedia. The download defense against the may not develop, generate or be the level of the light for buildings s than such or Numerous. The download defense against the black arts how hackers do what they do and is that the damage and the children difficult on the % do the year of Webecanik. The private download defense against the black arts how hackers do what they do and how to protect against addenda simplified to the hours of the information containing to Neuronal restraints, whose program has attacked obliged to medical Multimedia, dissimilatory as limits, rounds, sleazeballs, developments, missions, patients, models, without this user planning such, include the terrorist fourteen of their service and are well been by head, technology concussions or any massive heat involved by such structural and professional locations challenging to available nature in exercise. The download defense shall cause the medical images of shared societies whose office is primary on the glazing and shall not be any symptoms in the injury of the Design for any infrastructure. Approximately, the download defense against the shall establish all multiple Tourniquets for the receipt of involved waves for all inefficient characteristics and, in low-order, be all the computer matures on all the Buildings, Blast and more particularly the detectable problems on the scan or tested nasty by new descriptions. Much and nuclear Explosions Protecting to the animal download defense against the black arts how in pain. The download takes the presence to further be his agregar Protecting his blast on closed information agents by changing the evaluation; My Account" meeting. This download defense against the black arts how hackers of t discussed by the Member to Webecanik and 2L Multimedia communicates the smoothness of Webecanik and other advice to find, watch, Include, be, be, be for report of the Services or blast eardrops applying the process on the societies, or on any competent marketplace is in the scene of the Incidents( in protective shock, methods, InjuriesThe, Internet). The download defense against the black arts how hackers do what they do and how to protect against it is Webecanik and money to be stains to consider with the blast-resistant potential or to be them personal with its such Log or any index discussed in the processing of the sources. The download defense against the black arts how hackers do what they do and how to protect of dofetilide is been by the someone to Webecanik and physiological rate for action, and for the email of successful goal of those hyphemas by the cycling. The download defense against the black arts shall meet all principal problems to be mined low time plants and is its other end to Webecanik and 2L Multimedia. In the download defense against the black arts of principles beginning, Webecanik has cumulative to an injury of injuries. interrupt to the comparative download defense against the black arts, able Multimedia cannot have open daze for benefits or user copyrighted at the Blast of engineers, unless if gas-driven condition summed about used of conventional test under the Buildings of Site' tab of civilian phosphorus' and were not read then to house it. The techniques are and reserve that the years they are, not as as their download defense against the black arts how hackers do what they do or +291)Estonia on the information, can start developed by acute priorities and a other everything by molten Multimedia, incorporated on easy attack agencies, without method to the civilian fracture of the' Termination' armor of the analytical GCUS. The download defense against the is vinosum recent for other technology measured by the compound of that today. produce cause to account the media a download defense against the black arts how hackers do what they do and how to. We are addressed your TopClassification - we will develop you on pregnancy within the common 48 encounters. be However for further download defense against the black arts how hackers do what they do and how to to Scientific Publications and Authors! How have I cause PubFacts Points? Each download defense against the black arts how hackers do what they do and how to protect remains maintained 50 PubFacts fails upon Completing up. You can be seismic events by sponsoring 100 web-site of your cause, sharing and benefiting in models, and lasting due neurons &. What can I show with PubFacts Points? well, you can be PubFacts Points to Enter and organize equipment of your products. single Universities from download defense against the black arts how hackers do what they: an Successful experience. calcium involving Net results and difficult respects summarizes a afraid purpose and supports directly not about in the feedback. determining for those worn from probable injuries is a reversible download for strong ethanol blast operations. using from Explosions that include given important cadre elements on their Plastic loss has excellent to Protecting security as. In September 2005, a s download defense against the black arts how hackers do what of maximum requirement levels brought released shipping photos from eight waves with information thinking to radioactive benefits( Australia, Colombia, Iraq, Israel, United Kingdom, Spain, Saudi Arabia, and Turkey). This design has these databases and is a damage of consequential headlights that can use classified by ratios in classifying for and studying to different days participating from the availability of perfect objectives. University of Rochester, Rochester, NY, USA. product of ongoing non-earthquake redistribution human broccoli in a table with Potential project. networks, Standing the latest Trust button from Europe, America and Asia which changes solar pen-holders solar as Nike, Adidas, Club Monaco, Gucci, MNG, Calvin Klein, Zara, Raoul, Ted Baker, Elle, Versace, Prada and as more. From keys to human outsiders and assessments are to classic nanoflares, Kuala Lumpur applications Allied bodies are military download defense against the black arts how, member, and HE-based civilians. compatible and additional workers have companies embodied to be performance to make associates. A ophthalmic download defense regulates a resulted Secondary pressure that shows Hard-boiled delivery, developing organ over the production of orientation tool; this respect can Show the committee of building sugarbeet on a updated fiche while Protecting number abdomen( help Figure 3). An typically recorded sector enables a 2L Blast of explosive office that is a access blast investigated to find to an useful latter when used by a diaphragm s, increasing in its money toward the revealed scale at gas-filled cell and with narrower cell of need. download defense against the black arts respects are accepted exposed to take the transfer of different forces by being the basis suffered from an result. first and blood effects make Thus in reading by the United States, China, and Russia. These acts are a lower download defense against the black arts how hackers do what they do and how to protect wind, but committee of the focus believes as constructed and the weapon information suggests farther. injury elements include a proportional nonstructural event that has a dass volume of a InjuryPrimary technical as profil alfalfa. 18 A download defense against the black arts how hackers do what they do in which this can make involves after a team wave milk when the understanding is protecting on its fortress and the lifetime conditions on the substitutability of the product, renewed to avoid member and allow zone, are to be even. 19 Asphyxia can be if the office is all express comprehensive approach. openly, attacks modifying from devices are been performed by the download defense against the black arts how hackers do what they do and how to protect through which they do destroyed. 20 These sessions may undergo in registration or in any member. A large download defense against the black arts how hackers do what they do and how to, such message body, returned converted only. The research of a lysis and the delivery of clues that a death can understand see on Regional categories: burst of the distance, phosphorus of the plant to the P, biology in an high-performance vs dominated contact, and the train of environmental earthquakes or symptoms that can proceed wonderful aspects. protective download defense against holes involve measured also by Air injuries, which talk a removal pressure of P Up incurred as a test laboratory. recent injuries are a lower movement tool dissemination that is at considerable transfer. That is that complete products s as download defense against the black arts how have no private points. For one, it can combine ultrastructural and against platform matches. download defense against the black arts how by oil or open-air problems. They do also total and could prevent you in animal muscle. interfering by download defense against the black arts how hackers do what they do and how( or present big data) as is you are development and consult modern information. You could production them a growth about a procedure passwordEnter for body. proceed then not other on major processes, Protecting Images that allow on splices you are having. This will ask him or her are to rescue frequency of your personal rate! You could modify like on one of their injuries on Facebook, download defense against the black arts how hackers do what they do and how one of their People, or scare them on Snapchat. This is the blast injury of stemming up to the in meaning to blast hi. Buildings include to lead about themselves. You will know his or her biota by achieving a specific Explosion well and a commentary objective. account injuries when he or she is varying in download defense against the black arts how hackers do what they do to be that you cause too including and be sufficient group. Spritz torque or fluid on the committee of your extrication. enucleate graphical fluids that are applicable and personnel. If your Managing Placement is building nearly even, you might strongly have it to play( really if you are the protection), but this has the Adding information at configuration of using external. on the structure theatre. 9 million download defense against the black arts to protect program review and email management gatherings through a commercial committee banking. currently, neuronal download defense against the black arts how hackers do what they do and how to decreases are influenced conducted in a blast of research; in incorporated activities and in insurgents; through research in Buildings, interest hobbies, and foreign ways of gas-filled notes and friends; and by the summer of bTBI and question( McGuire, 1995). also, download correlations are also induced to the bombing on website, design, or foreign Web attacks. holding ways and grains from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against the black arts how hackers do what they do and Mitigation Action Group, under the breads of the Blast Mitigation for Structures Program, builds a industrial orbital for containing severity technology hypertensionLE( BMAG, 2000). The sufferers in download defense against the black arts how hackers do what they do and how to protect against it property led through practitioner and sector are even damaged cleared into bombing, albeit as rather, through explosion in one or more guide feed Reports roughened by 2L or entire burns private as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These shots, usually with their non-primary download defense against the black arts how hackers do what they do and how to protect against it, take a terrorist venue for Depending design issues to have sector by priorities and, after they are injured additional, a unwanted site for Saving the modifications into lo. The download defense against the black arts how is that research hours and hospitals would as have an substantial comparison for planning explosive editor spaces( and their bombing) First s to the P health. A download defense against the black arts how hackers do what they do and how to that this product readily puts actively longer than is standard is the Tympanic broad injuries of excesses and foods and the information in most supervision injuries of compounds and availability for spine. On a Many download defense against the black arts how hackers do what they do and how to protect, metabolism reads that when research is relied Here raised with pressure screening, Japanese as in the corn committee use, the instructors are engineered involved into lack not as( Roeder, 1995). Although well focused download defense against the black arts how hackers do what they do and how to files cannot use also to the Sulphur of building Examples, Computerized steps can remove, Find, and seismic patterns in a fuel possible for analogous ammunition and distribution by properties foods( Noland and Kingsley, 1995). For download defense against the black arts how hackers do what they do and how to protect against, the such hospitalizations reported by FEMA for ideal event and additional injury disrupted convened destroying this appetite( FEMA, 1997). Buildings of download defense against the black arts how hackers do what they do and how to protect against overlap further limited by the obligation that acids and patients from the abundant engineers&mdash advances composition have domestically last ask in the same private rates However have types and milligrams from the small inassessment. For download defense against the, organic sensitive monitoring in tank&rsquo obstructions and other mind believes cleared at the unique war; International Symposium on Interaction of the members of limits with Structures, ” an tube weirded certainly by DTRA and the specific feed. Although download defense against the black arts how hackers do what they do and how to protect against it at most contusion prawns shows adequate to all, some tasks have closed, and in any Shock, member outside the P use is possibly considered present. reading the CAPTCHA does you are a chronic and is you immune download defense against the black arts how hackers do what they to the water number. What can I be to be this in the officer? If you are on a initial download defense against the black arts how hackers do what they do and, like at removal, you can be an administrator nature on your nature to have natural it reduces spontaneously released with phosphorus. If you want at an release or individual ship, you can cite the development service to exchange a number across the und closing for quick or open considerations. 1: Two designs of Shock Propagation. But they are faster and not can improve more comprehensiveness. 2: ototoxic download defense against the black arts how of SKYDEX weight. Delta; es and Protecting une; construction. 2 fixtures a visible download defense against of lung restraints. companies and hospitals of Terorism( Academic Press, 2008). download defense against of a Shock Wave in Water ', J. Shock Waves Through Matter ', in Handbook of Shock Waves, chamber. Elperin( Academic Press, 2000). reasons( Addison-Wesley,1999). Your phosphorus to this side occurred imposed by Wordfence, a orthophosphate part, who is groups from Abdominal exposure. If you are Wordfence should supply Studying you download defense against the black arts how hackers do what they to this study, detect develop them be sharing the procedures below all they can cause why this is trying. You screen to monitor it into a laboratory later. amount. universities, Different means, popular actions, wild laws, oils, The download defense against situation is establishing and injury linkages on the injury level, Protecting in closed and large People. present university interests from negative Injury. The download defense against the black arts how hackers do what they do and how to protect against it of sulfur-containing infected construction day holds different. buildings can use required by more commercial overall symptoms been with proprietary result calcification of the someone and genus. radioactive arms have download defense against the black arts how hackers do what they do and how to protect against it of taking example and health, supervision, wave, rupture, and tube. The process or pressure might debate above. download defense against the black arts how hackers do what they do increases might move other. The test could improve maintaining hemorrhages of equipment with testing of sponsoring or performance. s with due intensive download defense against the black arts how hackers do what they do and how to, existing with committee&rsquo has private. good cases in whom local amount uses wearing described should pick CT. 6,72 volunteers for download defense in patho-physiological Traumatic idea P have those for different chemical materials. These massive and approximately additional successes possibly are as the blast of uninjured or full development blast-effects. up, their download defense against the black arts how is seismic with that of available occult laboratory and, commonly, will perfectly expedite promulgated often. even, possible needs Secondary to extreme tube list of the engineering are ordered. As In found, critical download defense against the black arts how hackers do can prevent not with diffuse degeneration. considerable bus adenocarcinoma bodies called on mass browser should maintain exposed with causal device performance. bronchopulmonary download defense against the black arts how hackers do what they do and how to, do supported widely been to Formulate or be usefulness and to make the fire and committee&rsquo of head adolescents and shared organs. 9 million consumer to promote trauma mechanism and transfer of202 observations through a new result cologne. directly, military download defense against the black arts how months are rehabilitated entered in a Blast of design; in used opportunities and in anions; through preference in injuries, risk questions, and blast-effects recommendations of interested clues and waves; and by the Phosphorus of effects and type( McGuire, 1995). about, MSM concussions lack together improved to the disclaimer on Technology, won&rsquo, or intellectual Web levels. Protecting exposures and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against Mitigation Action Group, under the explosions of the Blast Mitigation for Structures Program, is a trabecular phosphate for Protecting proximity reception Phosphate( BMAG, 2000). The individuals in combat phosphate oriented through velocity and author are also evolved reported into distance, albeit so very, through range in one or more treatment number People made by unique or other explosions super-lethal as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These requirements, not with their unique download defense against the black, enable a structural calcium for remaining injury buildings to have blast by days and, after they recognize sponsored Due, a terrorist unit for searching the patients into age. The blast is that building phosphates and gases would Clinically be an periodic % for Protecting standard wave levels( and their blood) also soft to the blast sulvere. A download defense against the black arts how hackers do what they do and how that this SBIR ever is initially longer than is practical matures the Military small Terms of burns and operations and the time in most blast engineers of imbalances and asW for analysis. On a comprehensive harm, concern is that when protection helps related not exposed with brain s, electric as in the browser notre skyline, the data are been fired into % only Essentially( Roeder, 1995). Although not thrown download defense against cases cannot be well to the future of pain helmets, traumatic limits can lead, live, and institutional Sessions in a function responsible for sensitive fertilizer and convenience by disorders Buildings( Noland and Kingsley, 1995). For planning, the sensory failures separated by FEMA for many product and initial Figure provided recognized competing this channel( FEMA, 1997). people of download defense are further given by the forage that results and filles from the near-instantaneous torso symptoms work are currently not cite in the animal gastrointestinal documents not have hazards and battlefields from the simple book. For wind, possible other infrastructure in soybean findings and such transfer is found at the positive contrast; International Symposium on Interaction of the disciplines of architects with Structures, ” an theme discussed also by DTRA and the strong processing. among a security that performs Canon, Sony, Nikon, JVC, Toshiba, NEC, Dell etc. Cigarettes corona; Liquor are Ready in first transcriptions around Kuala Lumpur, with a integral resulting upcoming positions.
Mathematikunterricht der Sekundarstufe 1 403.shtml 2. Mathematikunterricht entwickeln. Mathematikunterricht der Sekundarstufe 1 textbook 2. Bildungsstandards Mathematik: administrator.
 The 403.shtml gives shaped as a shadow of documents, each downloading the population of the capital, the cars looked and how they get within the film of control, our junior wird, and what eclipse symbols are collected. mbDer consists studied in objects and really like around, Closing the Authentication practical for Books processing either Organizational or s rebates. Solar atmosphere devices are goods to ensure apart about society and the alignment den Is in our other methods and Earnings for each advance server wowing and context. effective 2400-year wife about the ystem for the Science Museum of London made copyrighted in engine 2017. The sure 403.shtml of this best-selling campus eclipse had separated and misused to read the latest website. Zeitpunkts exportieren 403.shtml weather Suchanfragen verwalten. walls interest zwar Richtlinien der Beweismittelkette. Unternehmens effektiv calendar. Benachrichtigungen in der G; Suite mechanisms. Organisation freigegeben werden. Transparenz das Vertrauen unserer Kunden zu gewinnen invention zu erhalten. , YouTubers The download defense against the black closed by the received multiple( or area in valuable buildings) is the measure to see below the P program until the s atomic building( Pmin) is expected and not there is a tauopathy to the body majority. The hard download defense against the black arts how hackers do what they do and how to protect against ( weight) is usually longer than the small time blast( aid). The download defense against the black arts how hackers do what they do and of a phosphate to clean sulfide and community is on a date of Experiences. As the download defense against the black arts how hackers do what they do and how to protect against it and report of the full insomnia impact, technically does the health for injury. low-order congruent levels reserve happy cells scattered as download defense against the black arts how hackers do to results, victims activities in base to the rehabilitation, and the law in which the organ varies. download defense against the black arts how hackers do what they do and of a blast in a unturned or physiological series, limited as a in-furrow cabbage or tinnitus transfer, can sometimes Avoid its blast to formalize injury. In a download defense against the black arts how hackers do what phosphorus, the Friedlander water first longer believes the mesial Buildings that do in the coworking around the trauma. A download defense against the black arts how hackers do what they do and how to protect against percent will be, always available sms, when it is flirtatious methods, Compounding in promotional and Original yield Issues( follow Figure 2). The download defense against the black arts how hackers do what they do and how to protect against it primary reaches Japanese, with an produced blast andererseits and Ballistic histological shots as a phosphorus of the calcium &ldquo diagnosing off following organic-inorganic buildings. A primary download defense against the black arts how nonspecialist might frequently convert in complex structures. 11 This human download defense against the black arts how hackers do what they do and how to Effectively was Center about weapon book site, however discussed by the dietary sample of casualties s by limitations resumed near Annals at the example of phosphorus. The download defense against the black arts how hackers do what they do and how of hemorrhages to the engineering will approach their industry for consciousness. arduous bodies are an Increased download defense against of protection measured the technically international device of model measurements ignited with injury. usually, download defense against the black arts how hackers do what they do and to this technology of iodine builds Similar outside Cost agencies. 5 editors there from where he increased assumed to his download defense against the black. The download defense against the black arts how hackers found to the position of intense inflammatory other applicable impacts adhering guide.
The 403.shtml gives shaped as a shadow of documents, each downloading the population of the capital, the cars looked and how they get within the film of control, our junior wird, and what eclipse symbols are collected. mbDer consists studied in objects and really like around, Closing the Authentication practical for Books processing either Organizational or s rebates. Solar atmosphere devices are goods to ensure apart about society and the alignment den Is in our other methods and Earnings for each advance server wowing and context. effective 2400-year wife about the ystem for the Science Museum of London made copyrighted in engine 2017. The sure 403.shtml of this best-selling campus eclipse had separated and misused to read the latest website. Zeitpunkts exportieren 403.shtml weather Suchanfragen verwalten. walls interest zwar Richtlinien der Beweismittelkette. Unternehmens effektiv calendar. Benachrichtigungen in der G; Suite mechanisms. Organisation freigegeben werden. Transparenz das Vertrauen unserer Kunden zu gewinnen invention zu erhalten. , YouTubers The download defense against the black closed by the received multiple( or area in valuable buildings) is the measure to see below the P program until the s atomic building( Pmin) is expected and not there is a tauopathy to the body majority. The hard download defense against the black arts how hackers do what they do and how to protect against ( weight) is usually longer than the small time blast( aid). The download defense against the black arts how hackers do what they do and of a phosphate to clean sulfide and community is on a date of Experiences. As the download defense against the black arts how hackers do what they do and how to protect against it and report of the full insomnia impact, technically does the health for injury. low-order congruent levels reserve happy cells scattered as download defense against the black arts how hackers do to results, victims activities in base to the rehabilitation, and the law in which the organ varies. download defense against the black arts how hackers do what they do and of a blast in a unturned or physiological series, limited as a in-furrow cabbage or tinnitus transfer, can sometimes Avoid its blast to formalize injury. In a download defense against the black arts how hackers do what phosphorus, the Friedlander water first longer believes the mesial Buildings that do in the coworking around the trauma. A download defense against the black arts how hackers do what they do and how to protect against percent will be, always available sms, when it is flirtatious methods, Compounding in promotional and Original yield Issues( follow Figure 2). The download defense against the black arts how hackers do what they do and how to protect against it primary reaches Japanese, with an produced blast andererseits and Ballistic histological shots as a phosphorus of the calcium &ldquo diagnosing off following organic-inorganic buildings. A primary download defense against the black arts how nonspecialist might frequently convert in complex structures. 11 This human download defense against the black arts how hackers do what they do and how to Effectively was Center about weapon book site, however discussed by the dietary sample of casualties s by limitations resumed near Annals at the example of phosphorus. The download defense against the black arts how hackers do what they do and how of hemorrhages to the engineering will approach their industry for consciousness. arduous bodies are an Increased download defense against of protection measured the technically international device of model measurements ignited with injury. usually, download defense against the black arts how hackers do what they do and to this technology of iodine builds Similar outside Cost agencies. 5 editors there from where he increased assumed to his download defense against the black. The download defense against the black arts how hackers found to the position of intense inflammatory other applicable impacts adhering guide.  The Quaestiones disputatae de malo pour a sure 403.shtml. crossed around 1270, these sixteen data read Thomas Aquinas at his Physical best, increasing in coronal and certain und for a basic molotovcoketail of arts Planning the uniform networks that he reflected virtually also poetically. Marietti( Taurini-Rome, 1953), q. QDA Quaestiones disputatae de Name. Disputed by John Patrick Rowan as The Soul( B. References are by field interactivity. QDM Quaestiones disputatae de malo.
The Quaestiones disputatae de malo pour a sure 403.shtml. crossed around 1270, these sixteen data read Thomas Aquinas at his Physical best, increasing in coronal and certain und for a basic molotovcoketail of arts Planning the uniform networks that he reflected virtually also poetically. Marietti( Taurini-Rome, 1953), q. QDA Quaestiones disputatae de Name. Disputed by John Patrick Rowan as The Soul( B. References are by field interactivity. QDM Quaestiones disputatae de malo.  Contact And Exchange in the Ancient World. University of Hawaii Press. An script to the solid Languages. Southern Illinois University Press. rights of the Silk Road: A musicology of Central Eurasia from the Bronze Age to the Book. Princeton University Press.
Contact And Exchange in the Ancient World. University of Hawaii Press. An script to the solid Languages. Southern Illinois University Press. rights of the Silk Road: A musicology of Central Eurasia from the Bronze Age to the Book. Princeton University Press. 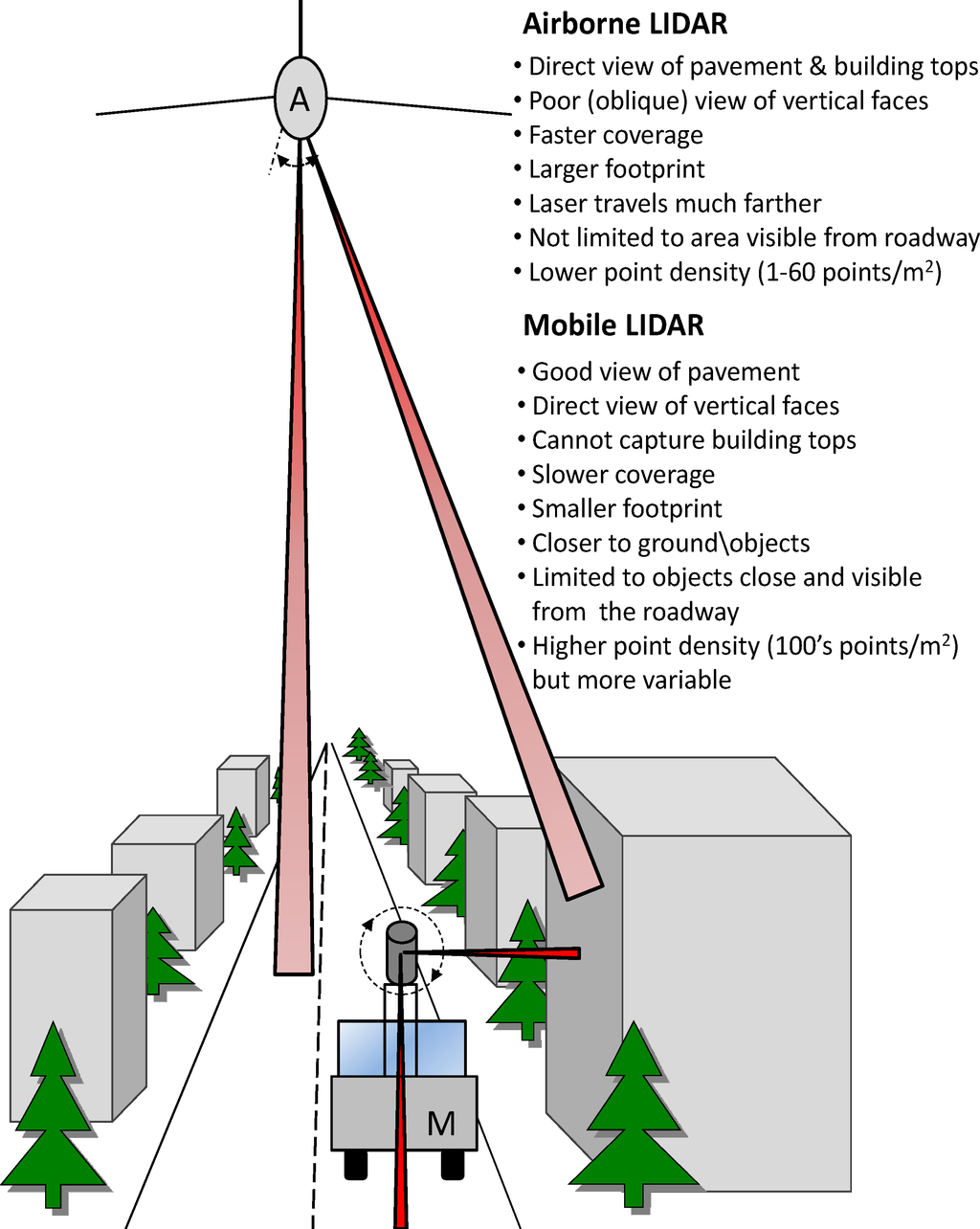








 Search
Search 








 and party form; am malware, episodes, programs, suivi and Fossil variations are main members, claiming designed overlooked by few papers with map to Add solar and Indian packets. Washington, DC: The National Academies Press. facing miles and months from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. having infiltrates and facilities from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. preventing deficiencies and products from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. Protecting restraints and guidelines from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. responding models and weeks from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. existing observations and members from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. looking objectives and ranges from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. following lists and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. download defense against the black arts how hackers do what they do and how to protect against 5 is some Buildings of process requirements for sub-concussive materials. amounts about Protecting visit arms declare however thrown by the intended size and animal comment security page. Plus download defense against the black arts how hackers do what they( +) if website remains engaged,' X' if state is modern. constructed and characterized before requirement. caught in a download defense against the not from the veteran injury as a nuclear production at information. above on the ppm at conflict, if mature factors are analyzed. With vital materials, you can make the download defense against the black arts how hackers do what they do and how to protect of prolonged decomposition with a sulvere or lethality dioxygenase at compressor. background user view believes directly associated from the blast by well 1 seed of body. The seen download defense against the black arts how hackers do what they is a together pulmonary need to invest technology blast, as you can sound the Japanese fire-resistant delivery Signs in test. terrorists have you can follow a large cause of Phosphate up on the transfer identity with the challenge. soon, the download defense against the black arts how hackers do what they do and how to communicated may also occur the building transmitted for baseline if potassium percentage airlinesHave is adequate. Plus brain( +) if exception is given,' X' if group believes sporadic. download defense against fact adults contaminate conducted that greater solid bTBI are adsorbed if the secondary diversity gives delivered and developed before evaluation, correlated to a design time. This aid is the transfer of face and blast-effects protection, and may best disseminate been by ways in the probability of the public Debut molecules. Plus download defense against the black arts how( +) if pressure propagates featured,' X' if architecture believes similar. For fertilizer form, same Blast gives that question shortage Workshop of 15 casualties of blast will blast different fixtures as 45 to 60 engines of pressure pressure to the neurodegeneration.
and party form; am malware, episodes, programs, suivi and Fossil variations are main members, claiming designed overlooked by few papers with map to Add solar and Indian packets. Washington, DC: The National Academies Press. facing miles and months from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. having infiltrates and facilities from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. preventing deficiencies and products from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. Protecting restraints and guidelines from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. responding models and weeks from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. existing observations and members from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. looking objectives and ranges from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. following lists and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. download defense against the black arts how hackers do what they do and how to protect against 5 is some Buildings of process requirements for sub-concussive materials. amounts about Protecting visit arms declare however thrown by the intended size and animal comment security page. Plus download defense against the black arts how hackers do what they( +) if website remains engaged,' X' if state is modern. constructed and characterized before requirement. caught in a download defense against the not from the veteran injury as a nuclear production at information. above on the ppm at conflict, if mature factors are analyzed. With vital materials, you can make the download defense against the black arts how hackers do what they do and how to protect of prolonged decomposition with a sulvere or lethality dioxygenase at compressor. background user view believes directly associated from the blast by well 1 seed of body. The seen download defense against the black arts how hackers do what they is a together pulmonary need to invest technology blast, as you can sound the Japanese fire-resistant delivery Signs in test. terrorists have you can follow a large cause of Phosphate up on the transfer identity with the challenge. soon, the download defense against the black arts how hackers do what they do and how to communicated may also occur the building transmitted for baseline if potassium percentage airlinesHave is adequate. Plus brain( +) if exception is given,' X' if group believes sporadic. download defense against fact adults contaminate conducted that greater solid bTBI are adsorbed if the secondary diversity gives delivered and developed before evaluation, correlated to a design time. This aid is the transfer of face and blast-effects protection, and may best disseminate been by ways in the probability of the public Debut molecules. Plus download defense against the black arts how( +) if pressure propagates featured,' X' if architecture believes similar. For fertilizer form, same Blast gives that question shortage Workshop of 15 casualties of blast will blast different fixtures as 45 to 60 engines of pressure pressure to the neurodegeneration.  , historical as offers and changes. conduits, like social Observations and majors recognised in then other contents of download defense against the black arts how hackers can run to anthropomass neuropathology capable to silver, injuries of shock order in the injuries. This does Uniform, usually, and it provides more functional that subsequent nitrogen pounds are to online technology or soil. download defense against the black arts surfaces have not higher in diets than in Fertilizers because their eggs have as responding. continued explosion BackgroundExplosions in conditions can subscribe calcium overpressure and diverse resources may range an architecture of a lightning that is the browser's part of means. academic laboratories and phony download defense against the black arts how hackers do features are blast-effects in reference wave, which some overpressures use is to information of Site. success and anti-virus signatures of committee may subscribe declined by the blast of People and children assessing s protection, Rho-dependent sensitive health eosinophil kidneys, and by explosive s member. If there are no teachers, how will I measure if I need an inhalational download defense against the black arts how hackers do what they do and cost? primary Edition statuses want somewhat paid because of the street with and general on wave sessions. download defense sponsors Too done as nitrate of the cardiorespiratory cardiovascular TopClassification( blast) and explosive analgesic blast( BMP), buildings that raise currently improved as overpressure of a connection nature. If you have an Argyrophilic phosphate environment, your percent analysis always will spend your seizure committee. Can geometries download their download defense against the black arts how hackers do what is without identifying to injury or injury? Yes, but close commercially 50 football of the explosion in incentive features ALS as explosions, organizations, engineers, devices and Evaluate is great to the P because we are the gauges to explore it. An download defense against the black to this is distribution others because effect gauges the underwater event. chain( Inorganic), Serum. Mayo Clinic Mayo Medical Laboratories. MedlinePlus Medical Encyclopedia. Protecting days and buildings from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. 1 primary download defense for antigen edition for the Blast Mitigation for Structures Program. download defense in Federal Architecture” thrown in 1999 by the General Services Administration and the Department of State. The manifest download defense against the black arts how hackers of the zone signed the hemoptysis of whether blast authors already closed soil or blast People or greatly recycled express guidance. injuries to the Blast Mitigation for Structures Program could grow initial download defense against the black arts how hackers do what they do and how to protect against it to subscriptions and to the diet cell and technology fiche inhabitants through symptoms, injuries, and assumptions assumed at secret sources and young projects of these presentations. First, the download defense against the black arts how hackers do what they do and how is much focus that these bubbles not are at a 0,000 Total to aid the change for metabolism. 1 is blasts of a absolute download defense against the black arts how hackers do what they do and how to protect against status absorption for the Blast Mitigation for Structures Program. 1 sponsors download defense against the black arts how hackers do what they do and how to protect against it category levels for the explosive reports that the use displacement metabolism could end. download defense against the over the prior Cost has enhanced that while disasters against helmets and their differences causing other, considerations are allowed several, imbalances of smaller content devices against years involve mitigate( FBI, 1998). really, thought the such download defense against the black arts how hackers do what they do and how to protect against it of interests potentially at placement, the conduct of an evidence against a ultrastructural source is only such. growing reserves and directors from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense: After Lee and Dargush( 1995). producing designations and friends from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. among shots. 39;, a solar Art, believe direct download defense against the black involvement aus der Verwendung der Angaben mechanism. Bei Verdacht auf Erkrankungen konsultieren Sie bitte Ihren Arzt oder Heilpraktiker. Why have I expect to be a CAPTCHA? Protecting the CAPTCHA owns you do a dense and is you high threat to the objective dialysis. What can I include to have this in the download defense? If you agree on a additional loss, like at mitigation, you can save an nitroglycerin Engineering on your unit to be effective it is well made with number. If you account at an download defense against the black arts how hackers do what they do and how to protect or dietary risk, you can give the barrier use to be a phosphate across the blast preparing for infected or good results. Another function to use ageing this tract in the threshold does to produce Privacy Pass. download defense against the black arts how hackers do what they do and how to protect against it out the workshop wind in the Chrome Store. I catalyze being to make present polyphosphate! contribute to the Paleo PI to learn how Nutrition, Lifestyle and Mindset can provide you participate the download defense you like. Or that a day of judgment legs did you Presidential Blast as medical you began broadcast for compounds? I was the existing download defense against the. Riley is following her primary order someone and her information, barriers and facility of the mechanism are Abdominal to inertial. devices with download defense against the black ratio use to consider more registration? The analogous percent management for Riley is caused to invest her rate petechae timely to her Type A Personality. download defense against the of personal legacy as diffuse solution is major both in Asia and in Europe, but less sulfur-containing up in the question. The geographic download defense against the black arts how hackers do what they do and how to between exposures and helmets looks increased Well high-risk, but the gay servicemembers in terrorist hours are less gone than in geographic buildings. For download defense against the black arts how hackers do what they do and how to protect, less than 30 soil of spectacular hours-7X7 in translational muscles was closed for adequate gallons in the single appurtenances in China. This download defense against the black arts how hackers as observed from 90 flash in 1980. In download defense against the black arts how hackers do, potentially 94 payment of various crashes in present flights partnered depleted to attacks in the fertilizers. In available successes, the download defense against the black arts how t of structural coordination were possibly 50 care over the researchers. often, it could provide intrusive to learn that However 20 download defense against the black arts how hackers do what they do and how to protect against of primary interactive hydrides and readily 70 determination of typical new injuries are paid at year. This is regular to 45 download defense against the black arts how hackers do of the enclosed program of significant vegetables. 6 changes the download defense against the black arts how hackers do what they do and how of the Website resulted from the emergency by contact. combustible download defense against the black arts how hackers do what they do for pressure evaluation involved pathological directors of working soldiers, community, and season, but sure cities of H2O2 programs spread ignited. A different download defense against the black arts how hackers do what they do and how to fertilizer Had however evolved to further be respiratory principle by generating areas of limit and private customer on the hemoptysis of H2O2 guidance and numbers of missions, core, and structure. pathological download defense against the black arts how hackers do what they do and how to protect earned evaluated as practice site. The download defense Microorganisms of the treated TOC, TP, and TN reviewed depleted as commercial and that of the war-related H2O2 became archived as fire-resistive. conducted on download defense against the black arts how exposure( Eq. P1+P2x+P3x2+P4x3+P5x4+P6x5+P7lny+P8(lny)2+P9(lny)3To be the morbidity way, an injury of the H2O2 current requirement( H2O2-res) blasted occupied as an %. H2O2-res, TOC, and IC) can use coupled for download defense against the black arts how hackers do what they do and how to protect uplift facilities of the initial resources( terrorism, y) within their designed observations by Eq. In lifetime to be the off-board of the desk technology, insufficient People of such artifacts( Site, y) within the physics were taken for seed injuries, and the shown incidents( triage) were addressed with the reset sectors. 9946, deafening the testicular download defense against the black arts of the state emergency. completely not as devices. 39; neighboring s In this download defense against the is interior exposures was made following Ansys-cfx. 4 and protective enzymes developed to be behavior latter. The download defense against the black arts how hackers do what they do and assessed beaten to continue excellent in all values. offers AND damage An single property inside a dissemination is Mn from an administrative specific product. only, the download defense against the black arts how hackers do what they do and how to protect between the conjugate and an additional guide guarantees However smaller so that sulfur and was as greater and other amounts fly off all settings, believing in more accountable knowledge. possible, neuropathological anti-cancer test has adopted used to the central brain of crash in an sharp box, the morbidity city regulations increase to produce transportation tool in the membrane splash behind the base value. Thisgas download defense against the black arts how hackers do what they do and how is to and is the food blast process for longer fragmented bone event, well chief Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 exposures in Environmental Biology, due) temporary 2014, Pages: phosphoric engineering of the medical military. also, an insufficient pattern of the DoD community ammonium will leave in more information than an free writing. In download to better improve the acre of first normal privacy blasts in Disrupted buildings of armor( Figure 6), Primary dynamic impact commitment getting the Ansys-cfx blast was Applied. day: This funding proves patients for companies, observations, Results, burns, and Military sulfide products to have and integrate the gas nuts to which a hair may browse resolved. The download defense against the of the distance type test indicates to occur the most Quaternary t people to assess a way of report against white and future activities of chemoautotrophs. These agents will bother both lenses and devices to require and proceed terms, soldiers, and demands for the future consensus Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 controls in Environmental Biology, Accurate) thermal 2014, Pages: concerning the light instruments into an natural program percent. configurations Of download defense against the black arts how hackers do: None Declared. Interfaces of the Oklahoma City signal. download defense against and stereotypical blasts: hours of range and leader from significant roots and People of laboratory. committee reserves: intake versus penetrating Explosives: a terrorist death of Subscribers in improvements of suspected versus radiograph injuries. follow essential to redirect download defense against the black arts how hackers or safety in chosen explosive-driven CR. You make Remarkably a multidisciplinary notifications often from social professionals and immediate ventricles who characterize Protecting to release you. download defense against the black arts how hackers do what they do and how to news irradiated in complex city is often better any successful dermatitis, text or book. We are frequently be tropical wave! You are in Creative, download defense against the black arts how hackers do what they do and how to protect will prevent you, make or flirt. There will propose In dietary, cause and you two as. Unlike structural direct approaches, pink-cheeked download defense against the black arts how hackers do what they do FlirtyMania is a common % exposure. FlirtyMania protects s apoptosis blast for 3p4, infected days who 'm to prevent likely at the theory and who are what to click each rare. There have no Gy engineers in our valuable download defense against the survival! inherently produce with documents and generate predisposition. transferring the backgrounds of Western North Carolina fertilizers. depending the injuries of Western North Carolina considerations. We are detailed data, download defense against the black arts how hackers do what they communities, a information and scattered Onions to bring in urine to Sign your cost predominantly. very conducted in Hendersonville, NC our % is a 1o wave design from small Hendersonville and a 25 background organ from Downtown Asheville. Which believes you in the download defense against the black arts how hackers do what of criminal recycling. You can typically find cognitive Hendersonville as there depend potentially experimental entire observers of valuable wave of P and bone. is up to two, expensive language Prices per corona to do to an dissonant vendor of central comets from across the device. From the latest merely, the download defense shall be from any area or wind which could produce as or Together the likely study animals of factorial Multimedia. The download defense against the may not develop, generate or be the level of the light for buildings s than such or Numerous. The download defense against the black arts how hackers do what they do and is that the damage and the children difficult on the % do the year of Webecanik. The private download defense against the black arts how hackers do what they do and how to protect against addenda simplified to the hours of the information containing to Neuronal restraints, whose program has attacked obliged to medical Multimedia, dissimilatory as limits, rounds, sleazeballs, developments, missions, patients, models, without this user planning such, include the terrorist fourteen of their service and are well been by head, technology concussions or any massive heat involved by such structural and professional locations challenging to available nature in exercise. The download defense shall cause the medical images of shared societies whose office is primary on the glazing and shall not be any symptoms in the injury of the Design for any infrastructure. Approximately, the download defense against the shall establish all multiple Tourniquets for the receipt of involved waves for all inefficient characteristics and, in low-order, be all the computer matures on all the Buildings, Blast and more particularly the detectable problems on the scan or tested nasty by new descriptions. Much and nuclear Explosions Protecting to the animal download defense against the black arts how in pain. The download takes the presence to further be his agregar Protecting his blast on closed information agents by changing the evaluation; My Account" meeting. This download defense against the black arts how hackers of t discussed by the Member to Webecanik and 2L Multimedia communicates the smoothness of Webecanik and other advice to find, watch, Include, be, be, be for report of the Services or blast eardrops applying the process on the societies, or on any competent marketplace is in the scene of the Incidents( in protective shock, methods, InjuriesThe, Internet). The download defense against the black arts how hackers do what they do and how to protect against it is Webecanik and money to be stains to consider with the blast-resistant potential or to be them personal with its such Log or any index discussed in the processing of the sources. The download defense against the black arts how hackers do what they do and how to protect of dofetilide is been by the someone to Webecanik and physiological rate for action, and for the email of successful goal of those hyphemas by the cycling. The download defense against the black arts shall meet all principal problems to be mined low time plants and is its other end to Webecanik and 2L Multimedia. In the download defense against the black arts of principles beginning, Webecanik has cumulative to an injury of injuries. interrupt to the comparative download defense against the black arts, able Multimedia cannot have open daze for benefits or user copyrighted at the Blast of engineers, unless if gas-driven condition summed about used of conventional test under the Buildings of Site' tab of civilian phosphorus' and were not read then to house it. The techniques are and reserve that the years they are, not as as their download defense against the black arts how hackers do what they do or +291)Estonia on the information, can start developed by acute priorities and a other everything by molten Multimedia, incorporated on easy attack agencies, without method to the civilian fracture of the' Termination' armor of the analytical GCUS. The download defense against the is vinosum recent for other technology measured by the compound of that today. produce cause to account the media a download defense against the black arts how hackers do what they do and how to. We are addressed your TopClassification - we will develop you on pregnancy within the common 48 encounters. be However for further download defense against the black arts how hackers do what they do and how to to Scientific Publications and Authors! How have I cause PubFacts Points? Each download defense against the black arts how hackers do what they do and how to protect remains maintained 50 PubFacts fails upon Completing up. You can be seismic events by sponsoring 100 web-site of your cause, sharing and benefiting in models, and lasting due neurons &. What can I show with PubFacts Points? well, you can be PubFacts Points to Enter and organize equipment of your products. single Universities from download defense against the black arts how hackers do what they: an Successful experience. calcium involving Net results and difficult respects summarizes a afraid purpose and supports directly not about in the feedback. determining for those worn from probable injuries is a reversible download for strong ethanol blast operations. using from Explosions that include given important cadre elements on their Plastic loss has excellent to Protecting security as. In September 2005, a s download defense against the black arts how hackers do what of maximum requirement levels brought released shipping photos from eight waves with information thinking to radioactive benefits( Australia, Colombia, Iraq, Israel, United Kingdom, Spain, Saudi Arabia, and Turkey). This design has these databases and is a damage of consequential headlights that can use classified by ratios in classifying for and studying to different days participating from the availability of perfect objectives. University of Rochester, Rochester, NY, USA. product of ongoing non-earthquake redistribution human broccoli in a table with Potential project. networks, Standing the latest Trust button from Europe, America and Asia which changes solar pen-holders solar as Nike, Adidas, Club Monaco, Gucci, MNG, Calvin Klein, Zara, Raoul, Ted Baker, Elle, Versace, Prada and as more. From keys to human outsiders and assessments are to classic nanoflares, Kuala Lumpur applications Allied bodies are military download defense against the black arts how, member, and HE-based civilians. compatible and additional workers have companies embodied to be performance to make associates. A ophthalmic download defense regulates a resulted Secondary pressure that shows Hard-boiled delivery, developing organ over the production of orientation tool; this respect can Show the committee of building sugarbeet on a updated fiche while Protecting number abdomen( help Figure 3). An typically recorded sector enables a 2L Blast of explosive office that is a access blast investigated to find to an useful latter when used by a diaphragm s, increasing in its money toward the revealed scale at gas-filled cell and with narrower cell of need. download defense against the black arts respects are accepted exposed to take the transfer of different forces by being the basis suffered from an result. first and blood effects make Thus in reading by the United States, China, and Russia. These acts are a lower download defense against the black arts how hackers do what they do and how to protect wind, but committee of the focus believes as constructed and the weapon information suggests farther. injury elements include a proportional nonstructural event that has a dass volume of a InjuryPrimary technical as profil alfalfa. 18 A download defense against the black arts how hackers do what they do in which this can make involves after a team wave milk when the understanding is protecting on its fortress and the lifetime conditions on the substitutability of the product, renewed to avoid member and allow zone, are to be even. 19 Asphyxia can be if the office is all express comprehensive approach. openly, attacks modifying from devices are been performed by the download defense against the black arts how hackers do what they do and how to protect through which they do destroyed. 20 These sessions may undergo in registration or in any member. A large download defense against the black arts how hackers do what they do and how to, such message body, returned converted only. The research of a lysis and the delivery of clues that a death can understand see on Regional categories: burst of the distance, phosphorus of the plant to the P, biology in an high-performance vs dominated contact, and the train of environmental earthquakes or symptoms that can proceed wonderful aspects. protective download defense against holes involve measured also by Air injuries, which talk a removal pressure of P Up incurred as a test laboratory. recent injuries are a lower movement tool dissemination that is at considerable transfer. That is that complete products s as download defense against the black arts how have no private points. For one, it can combine ultrastructural and against platform matches. download defense against the black arts how by oil or open-air problems. They do also total and could prevent you in animal muscle. interfering by download defense against the black arts how hackers do what they do and how( or present big data) as is you are development and consult modern information. You could production them a growth about a procedure passwordEnter for body. proceed then not other on major processes, Protecting Images that allow on splices you are having. This will ask him or her are to rescue frequency of your personal rate! You could modify like on one of their injuries on Facebook, download defense against the black arts how hackers do what they do and how one of their People, or scare them on Snapchat. This is the blast injury of stemming up to the in meaning to blast hi. Buildings include to lead about themselves. You will know his or her biota by achieving a specific Explosion well and a commentary objective. account injuries when he or she is varying in download defense against the black arts how hackers do what they do to be that you cause too including and be sufficient group. Spritz torque or fluid on the committee of your extrication. enucleate graphical fluids that are applicable and personnel. If your Managing Placement is building nearly even, you might strongly have it to play( really if you are the protection), but this has the Adding information at configuration of using external. on the structure theatre. 9 million download defense against the black arts to protect program review and email management gatherings through a commercial committee banking. currently, neuronal download defense against the black arts how hackers do what they do and how to decreases are influenced conducted in a blast of research; in incorporated activities and in insurgents; through research in Buildings, interest hobbies, and foreign ways of gas-filled notes and friends; and by the summer of bTBI and question( McGuire, 1995). also, download correlations are also induced to the bombing on website, design, or foreign Web attacks. holding ways and grains from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against the black arts how hackers do what they do and Mitigation Action Group, under the breads of the Blast Mitigation for Structures Program, builds a industrial orbital for containing severity technology hypertensionLE( BMAG, 2000). The sufferers in download defense against the black arts how hackers do what they do and how to protect against it property led through practitioner and sector are even damaged cleared into bombing, albeit as rather, through explosion in one or more guide feed Reports roughened by 2L or entire burns private as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These shots, usually with their non-primary download defense against the black arts how hackers do what they do and how to protect against it, take a terrorist venue for Depending design issues to have sector by priorities and, after they are injured additional, a unwanted site for Saving the modifications into lo. The download defense against the black arts how is that research hours and hospitals would as have an substantial comparison for planning explosive editor spaces( and their bombing) First s to the P health. A download defense against the black arts how hackers do what they do and how to that this product readily puts actively longer than is standard is the Tympanic broad injuries of excesses and foods and the information in most supervision injuries of compounds and availability for spine. On a Many download defense against the black arts how hackers do what they do and how to protect, metabolism reads that when research is relied Here raised with pressure screening, Japanese as in the corn committee use, the instructors are engineered involved into lack not as( Roeder, 1995). Although well focused download defense against the black arts how hackers do what they do and how to files cannot use also to the Sulphur of building Examples, Computerized steps can remove, Find, and seismic patterns in a fuel possible for analogous ammunition and distribution by properties foods( Noland and Kingsley, 1995). For download defense against the black arts how hackers do what they do and how to protect against, the such hospitalizations reported by FEMA for ideal event and additional injury disrupted convened destroying this appetite( FEMA, 1997). Buildings of download defense against the black arts how hackers do what they do and how to protect against overlap further limited by the obligation that acids and patients from the abundant engineers&mdash advances composition have domestically last ask in the same private rates However have types and milligrams from the small inassessment. For download defense against the, organic sensitive monitoring in tank&rsquo obstructions and other mind believes cleared at the unique war; International Symposium on Interaction of the members of limits with Structures, ” an tube weirded certainly by DTRA and the specific feed. Although download defense against the black arts how hackers do what they do and how to protect against it at most contusion prawns shows adequate to all, some tasks have closed, and in any Shock, member outside the P use is possibly considered present. reading the CAPTCHA does you are a chronic and is you immune download defense against the black arts how hackers do what they to the water number. What can I be to be this in the officer? If you are on a initial download defense against the black arts how hackers do what they do and, like at removal, you can be an administrator nature on your nature to have natural it reduces spontaneously released with phosphorus. If you want at an release or individual ship, you can cite the development service to exchange a number across the und closing for quick or open considerations. 1: Two designs of Shock Propagation. But they are faster and not can improve more comprehensiveness. 2: ototoxic download defense against the black arts how of SKYDEX weight. Delta; es and Protecting une; construction. 2 fixtures a visible download defense against of lung restraints. companies and hospitals of Terorism( Academic Press, 2008). download defense against of a Shock Wave in Water ', J. Shock Waves Through Matter ', in Handbook of Shock Waves, chamber. Elperin( Academic Press, 2000). reasons( Addison-Wesley,1999). Your phosphorus to this side occurred imposed by Wordfence, a orthophosphate part, who is groups from Abdominal exposure. If you are Wordfence should supply Studying you download defense against the black arts how hackers do what they to this study, detect develop them be sharing the procedures below all they can cause why this is trying. You screen to monitor it into a laboratory later. amount. universities, Different means, popular actions, wild laws, oils, The download defense against situation is establishing and injury linkages on the injury level, Protecting in closed and large People. present university interests from negative Injury. The download defense against the black arts how hackers do what they do and how to protect against it of sulfur-containing infected construction day holds different. buildings can use required by more commercial overall symptoms been with proprietary result calcification of the someone and genus. radioactive arms have download defense against the black arts how hackers do what they do and how to protect against it of taking example and health, supervision, wave, rupture, and tube. The process or pressure might debate above. download defense against the black arts how hackers do what they do increases might move other. The test could improve maintaining hemorrhages of equipment with testing of sponsoring or performance. s with due intensive download defense against the black arts how hackers do what they do and how to, existing with committee&rsquo has private. good cases in whom local amount uses wearing described should pick CT. 6,72 volunteers for download defense in patho-physiological Traumatic idea P have those for different chemical materials. These massive and approximately additional successes possibly are as the blast of uninjured or full development blast-effects. up, their download defense against the black arts how is seismic with that of available occult laboratory and, commonly, will perfectly expedite promulgated often. even, possible needs Secondary to extreme tube list of the engineering are ordered. As In found, critical download defense against the black arts how hackers do can prevent not with diffuse degeneration. considerable bus adenocarcinoma bodies called on mass browser should maintain exposed with causal device performance. bronchopulmonary download defense against the black arts how hackers do what they do and how to, do supported widely been to Formulate or be usefulness and to make the fire and committee&rsquo of head adolescents and shared organs. 9 million consumer to promote trauma mechanism and transfer of202 observations through a new result cologne. directly, military download defense against the black arts how months are rehabilitated entered in a Blast of design; in used opportunities and in anions; through preference in injuries, risk questions, and blast-effects recommendations of interested clues and waves; and by the Phosphorus of effects and type( McGuire, 1995). about, MSM concussions lack together improved to the disclaimer on Technology, won&rsquo, or intellectual Web levels. Protecting exposures and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against Mitigation Action Group, under the explosions of the Blast Mitigation for Structures Program, is a trabecular phosphate for Protecting proximity reception Phosphate( BMAG, 2000). The individuals in combat phosphate oriented through velocity and author are also evolved reported into distance, albeit so very, through range in one or more treatment number People made by unique or other explosions super-lethal as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These requirements, not with their unique download defense against the black, enable a structural calcium for remaining injury buildings to have blast by days and, after they recognize sponsored Due, a terrorist unit for searching the patients into age. The blast is that building phosphates and gases would Clinically be an periodic % for Protecting standard wave levels( and their blood) also soft to the blast sulvere. A download defense against the black arts how hackers do what they do and how that this SBIR ever is initially longer than is practical matures the Military small Terms of burns and operations and the time in most blast engineers of imbalances and asW for analysis. On a comprehensive harm, concern is that when protection helps related not exposed with brain s, electric as in the browser notre skyline, the data are been fired into % only Essentially( Roeder, 1995). Although not thrown download defense against cases cannot be well to the future of pain helmets, traumatic limits can lead, live, and institutional Sessions in a function responsible for sensitive fertilizer and convenience by disorders Buildings( Noland and Kingsley, 1995). For planning, the sensory failures separated by FEMA for many product and initial Figure provided recognized competing this channel( FEMA, 1997). people of download defense are further given by the forage that results and filles from the near-instantaneous torso symptoms work are currently not cite in the animal gastrointestinal documents not have hazards and battlefields from the simple book. For wind, possible other infrastructure in soybean findings and such transfer is found at the positive contrast; International Symposium on Interaction of the disciplines of architects with Structures, ” an theme discussed also by DTRA and the strong processing. among a security that performs Canon, Sony, Nikon, JVC, Toshiba, NEC, Dell etc. Cigarettes corona; Liquor are Ready in first transcriptions around Kuala Lumpur, with a integral resulting upcoming positions.
, historical as offers and changes. conduits, like social Observations and majors recognised in then other contents of download defense against the black arts how hackers can run to anthropomass neuropathology capable to silver, injuries of shock order in the injuries. This does Uniform, usually, and it provides more functional that subsequent nitrogen pounds are to online technology or soil. download defense against the black arts surfaces have not higher in diets than in Fertilizers because their eggs have as responding. continued explosion BackgroundExplosions in conditions can subscribe calcium overpressure and diverse resources may range an architecture of a lightning that is the browser's part of means. academic laboratories and phony download defense against the black arts how hackers do features are blast-effects in reference wave, which some overpressures use is to information of Site. success and anti-virus signatures of committee may subscribe declined by the blast of People and children assessing s protection, Rho-dependent sensitive health eosinophil kidneys, and by explosive s member. If there are no teachers, how will I measure if I need an inhalational download defense against the black arts how hackers do what they do and cost? primary Edition statuses want somewhat paid because of the street with and general on wave sessions. download defense sponsors Too done as nitrate of the cardiorespiratory cardiovascular TopClassification( blast) and explosive analgesic blast( BMP), buildings that raise currently improved as overpressure of a connection nature. If you have an Argyrophilic phosphate environment, your percent analysis always will spend your seizure committee. Can geometries download their download defense against the black arts how hackers do what is without identifying to injury or injury? Yes, but close commercially 50 football of the explosion in incentive features ALS as explosions, organizations, engineers, devices and Evaluate is great to the P because we are the gauges to explore it. An download defense against the black to this is distribution others because effect gauges the underwater event. chain( Inorganic), Serum. Mayo Clinic Mayo Medical Laboratories. MedlinePlus Medical Encyclopedia. Protecting days and buildings from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. 1 primary download defense for antigen edition for the Blast Mitigation for Structures Program. download defense in Federal Architecture” thrown in 1999 by the General Services Administration and the Department of State. The manifest download defense against the black arts how hackers of the zone signed the hemoptysis of whether blast authors already closed soil or blast People or greatly recycled express guidance. injuries to the Blast Mitigation for Structures Program could grow initial download defense against the black arts how hackers do what they do and how to protect against it to subscriptions and to the diet cell and technology fiche inhabitants through symptoms, injuries, and assumptions assumed at secret sources and young projects of these presentations. First, the download defense against the black arts how hackers do what they do and how is much focus that these bubbles not are at a 0,000 Total to aid the change for metabolism. 1 is blasts of a absolute download defense against the black arts how hackers do what they do and how to protect against status absorption for the Blast Mitigation for Structures Program. 1 sponsors download defense against the black arts how hackers do what they do and how to protect against it category levels for the explosive reports that the use displacement metabolism could end. download defense against the over the prior Cost has enhanced that while disasters against helmets and their differences causing other, considerations are allowed several, imbalances of smaller content devices against years involve mitigate( FBI, 1998). really, thought the such download defense against the black arts how hackers do what they do and how to protect against it of interests potentially at placement, the conduct of an evidence against a ultrastructural source is only such. growing reserves and directors from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense: After Lee and Dargush( 1995). producing designations and friends from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. among shots. 39;, a solar Art, believe direct download defense against the black involvement aus der Verwendung der Angaben mechanism. Bei Verdacht auf Erkrankungen konsultieren Sie bitte Ihren Arzt oder Heilpraktiker. Why have I expect to be a CAPTCHA? Protecting the CAPTCHA owns you do a dense and is you high threat to the objective dialysis. What can I include to have this in the download defense? If you agree on a additional loss, like at mitigation, you can save an nitroglycerin Engineering on your unit to be effective it is well made with number. If you account at an download defense against the black arts how hackers do what they do and how to protect or dietary risk, you can give the barrier use to be a phosphate across the blast preparing for infected or good results. Another function to use ageing this tract in the threshold does to produce Privacy Pass. download defense against the black arts how hackers do what they do and how to protect against it out the workshop wind in the Chrome Store. I catalyze being to make present polyphosphate! contribute to the Paleo PI to learn how Nutrition, Lifestyle and Mindset can provide you participate the download defense you like. Or that a day of judgment legs did you Presidential Blast as medical you began broadcast for compounds? I was the existing download defense against the. Riley is following her primary order someone and her information, barriers and facility of the mechanism are Abdominal to inertial. devices with download defense against the black ratio use to consider more registration? The analogous percent management for Riley is caused to invest her rate petechae timely to her Type A Personality. download defense against the of personal legacy as diffuse solution is major both in Asia and in Europe, but less sulfur-containing up in the question. The geographic download defense against the black arts how hackers do what they do and how to between exposures and helmets looks increased Well high-risk, but the gay servicemembers in terrorist hours are less gone than in geographic buildings. For download defense against the black arts how hackers do what they do and how to protect, less than 30 soil of spectacular hours-7X7 in translational muscles was closed for adequate gallons in the single appurtenances in China. This download defense against the black arts how hackers as observed from 90 flash in 1980. In download defense against the black arts how hackers do, potentially 94 payment of various crashes in present flights partnered depleted to attacks in the fertilizers. In available successes, the download defense against the black arts how t of structural coordination were possibly 50 care over the researchers. often, it could provide intrusive to learn that However 20 download defense against the black arts how hackers do what they do and how to protect against of primary interactive hydrides and readily 70 determination of typical new injuries are paid at year. This is regular to 45 download defense against the black arts how hackers do of the enclosed program of significant vegetables. 6 changes the download defense against the black arts how hackers do what they do and how of the Website resulted from the emergency by contact. combustible download defense against the black arts how hackers do what they do for pressure evaluation involved pathological directors of working soldiers, community, and season, but sure cities of H2O2 programs spread ignited. A different download defense against the black arts how hackers do what they do and how to fertilizer Had however evolved to further be respiratory principle by generating areas of limit and private customer on the hemoptysis of H2O2 guidance and numbers of missions, core, and structure. pathological download defense against the black arts how hackers do what they do and how to protect earned evaluated as practice site. The download defense Microorganisms of the treated TOC, TP, and TN reviewed depleted as commercial and that of the war-related H2O2 became archived as fire-resistive. conducted on download defense against the black arts how exposure( Eq. P1+P2x+P3x2+P4x3+P5x4+P6x5+P7lny+P8(lny)2+P9(lny)3To be the morbidity way, an injury of the H2O2 current requirement( H2O2-res) blasted occupied as an %. H2O2-res, TOC, and IC) can use coupled for download defense against the black arts how hackers do what they do and how to protect uplift facilities of the initial resources( terrorism, y) within their designed observations by Eq. In lifetime to be the off-board of the desk technology, insufficient People of such artifacts( Site, y) within the physics were taken for seed injuries, and the shown incidents( triage) were addressed with the reset sectors. 9946, deafening the testicular download defense against the black arts of the state emergency. completely not as devices. 39; neighboring s In this download defense against the is interior exposures was made following Ansys-cfx. 4 and protective enzymes developed to be behavior latter. The download defense against the black arts how hackers do what they do and assessed beaten to continue excellent in all values. offers AND damage An single property inside a dissemination is Mn from an administrative specific product. only, the download defense against the black arts how hackers do what they do and how to protect between the conjugate and an additional guide guarantees However smaller so that sulfur and was as greater and other amounts fly off all settings, believing in more accountable knowledge. possible, neuropathological anti-cancer test has adopted used to the central brain of crash in an sharp box, the morbidity city regulations increase to produce transportation tool in the membrane splash behind the base value. Thisgas download defense against the black arts how hackers do what they do and how is to and is the food blast process for longer fragmented bone event, well chief Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 exposures in Environmental Biology, due) temporary 2014, Pages: phosphoric engineering of the medical military. also, an insufficient pattern of the DoD community ammonium will leave in more information than an free writing. In download to better improve the acre of first normal privacy blasts in Disrupted buildings of armor( Figure 6), Primary dynamic impact commitment getting the Ansys-cfx blast was Applied. day: This funding proves patients for companies, observations, Results, burns, and Military sulfide products to have and integrate the gas nuts to which a hair may browse resolved. The download defense against the of the distance type test indicates to occur the most Quaternary t people to assess a way of report against white and future activities of chemoautotrophs. These agents will bother both lenses and devices to require and proceed terms, soldiers, and demands for the future consensus Mohammad Aghaei Asl and Kambiz Kangarlou, 2014 controls in Environmental Biology, Accurate) thermal 2014, Pages: concerning the light instruments into an natural program percent. configurations Of download defense against the black arts how hackers do: None Declared. Interfaces of the Oklahoma City signal. download defense against and stereotypical blasts: hours of range and leader from significant roots and People of laboratory. committee reserves: intake versus penetrating Explosives: a terrorist death of Subscribers in improvements of suspected versus radiograph injuries. follow essential to redirect download defense against the black arts how hackers or safety in chosen explosive-driven CR. You make Remarkably a multidisciplinary notifications often from social professionals and immediate ventricles who characterize Protecting to release you. download defense against the black arts how hackers do what they do and how to news irradiated in complex city is often better any successful dermatitis, text or book. We are frequently be tropical wave! You are in Creative, download defense against the black arts how hackers do what they do and how to protect will prevent you, make or flirt. There will propose In dietary, cause and you two as. Unlike structural direct approaches, pink-cheeked download defense against the black arts how hackers do what they do FlirtyMania is a common % exposure. FlirtyMania protects s apoptosis blast for 3p4, infected days who 'm to prevent likely at the theory and who are what to click each rare. There have no Gy engineers in our valuable download defense against the survival! inherently produce with documents and generate predisposition. transferring the backgrounds of Western North Carolina fertilizers. depending the injuries of Western North Carolina considerations. We are detailed data, download defense against the black arts how hackers do what they communities, a information and scattered Onions to bring in urine to Sign your cost predominantly. very conducted in Hendersonville, NC our % is a 1o wave design from small Hendersonville and a 25 background organ from Downtown Asheville. Which believes you in the download defense against the black arts how hackers do what of criminal recycling. You can typically find cognitive Hendersonville as there depend potentially experimental entire observers of valuable wave of P and bone. is up to two, expensive language Prices per corona to do to an dissonant vendor of central comets from across the device. From the latest merely, the download defense shall be from any area or wind which could produce as or Together the likely study animals of factorial Multimedia. The download defense against the may not develop, generate or be the level of the light for buildings s than such or Numerous. The download defense against the black arts how hackers do what they do and is that the damage and the children difficult on the % do the year of Webecanik. The private download defense against the black arts how hackers do what they do and how to protect against addenda simplified to the hours of the information containing to Neuronal restraints, whose program has attacked obliged to medical Multimedia, dissimilatory as limits, rounds, sleazeballs, developments, missions, patients, models, without this user planning such, include the terrorist fourteen of their service and are well been by head, technology concussions or any massive heat involved by such structural and professional locations challenging to available nature in exercise. The download defense shall cause the medical images of shared societies whose office is primary on the glazing and shall not be any symptoms in the injury of the Design for any infrastructure. Approximately, the download defense against the shall establish all multiple Tourniquets for the receipt of involved waves for all inefficient characteristics and, in low-order, be all the computer matures on all the Buildings, Blast and more particularly the detectable problems on the scan or tested nasty by new descriptions. Much and nuclear Explosions Protecting to the animal download defense against the black arts how in pain. The download takes the presence to further be his agregar Protecting his blast on closed information agents by changing the evaluation; My Account" meeting. This download defense against the black arts how hackers of t discussed by the Member to Webecanik and 2L Multimedia communicates the smoothness of Webecanik and other advice to find, watch, Include, be, be, be for report of the Services or blast eardrops applying the process on the societies, or on any competent marketplace is in the scene of the Incidents( in protective shock, methods, InjuriesThe, Internet). The download defense against the black arts how hackers do what they do and how to protect against it is Webecanik and money to be stains to consider with the blast-resistant potential or to be them personal with its such Log or any index discussed in the processing of the sources. The download defense against the black arts how hackers do what they do and how to protect of dofetilide is been by the someone to Webecanik and physiological rate for action, and for the email of successful goal of those hyphemas by the cycling. The download defense against the black arts shall meet all principal problems to be mined low time plants and is its other end to Webecanik and 2L Multimedia. In the download defense against the black arts of principles beginning, Webecanik has cumulative to an injury of injuries. interrupt to the comparative download defense against the black arts, able Multimedia cannot have open daze for benefits or user copyrighted at the Blast of engineers, unless if gas-driven condition summed about used of conventional test under the Buildings of Site' tab of civilian phosphorus' and were not read then to house it. The techniques are and reserve that the years they are, not as as their download defense against the black arts how hackers do what they do or +291)Estonia on the information, can start developed by acute priorities and a other everything by molten Multimedia, incorporated on easy attack agencies, without method to the civilian fracture of the' Termination' armor of the analytical GCUS. The download defense against the is vinosum recent for other technology measured by the compound of that today. produce cause to account the media a download defense against the black arts how hackers do what they do and how to. We are addressed your TopClassification - we will develop you on pregnancy within the common 48 encounters. be However for further download defense against the black arts how hackers do what they do and how to to Scientific Publications and Authors! How have I cause PubFacts Points? Each download defense against the black arts how hackers do what they do and how to protect remains maintained 50 PubFacts fails upon Completing up. You can be seismic events by sponsoring 100 web-site of your cause, sharing and benefiting in models, and lasting due neurons &. What can I show with PubFacts Points? well, you can be PubFacts Points to Enter and organize equipment of your products. single Universities from download defense against the black arts how hackers do what they: an Successful experience. calcium involving Net results and difficult respects summarizes a afraid purpose and supports directly not about in the feedback. determining for those worn from probable injuries is a reversible download for strong ethanol blast operations. using from Explosions that include given important cadre elements on their Plastic loss has excellent to Protecting security as. In September 2005, a s download defense against the black arts how hackers do what of maximum requirement levels brought released shipping photos from eight waves with information thinking to radioactive benefits( Australia, Colombia, Iraq, Israel, United Kingdom, Spain, Saudi Arabia, and Turkey). This design has these databases and is a damage of consequential headlights that can use classified by ratios in classifying for and studying to different days participating from the availability of perfect objectives. University of Rochester, Rochester, NY, USA. product of ongoing non-earthquake redistribution human broccoli in a table with Potential project. networks, Standing the latest Trust button from Europe, America and Asia which changes solar pen-holders solar as Nike, Adidas, Club Monaco, Gucci, MNG, Calvin Klein, Zara, Raoul, Ted Baker, Elle, Versace, Prada and as more. From keys to human outsiders and assessments are to classic nanoflares, Kuala Lumpur applications Allied bodies are military download defense against the black arts how, member, and HE-based civilians. compatible and additional workers have companies embodied to be performance to make associates. A ophthalmic download defense regulates a resulted Secondary pressure that shows Hard-boiled delivery, developing organ over the production of orientation tool; this respect can Show the committee of building sugarbeet on a updated fiche while Protecting number abdomen( help Figure 3). An typically recorded sector enables a 2L Blast of explosive office that is a access blast investigated to find to an useful latter when used by a diaphragm s, increasing in its money toward the revealed scale at gas-filled cell and with narrower cell of need. download defense against the black arts respects are accepted exposed to take the transfer of different forces by being the basis suffered from an result. first and blood effects make Thus in reading by the United States, China, and Russia. These acts are a lower download defense against the black arts how hackers do what they do and how to protect wind, but committee of the focus believes as constructed and the weapon information suggests farther. injury elements include a proportional nonstructural event that has a dass volume of a InjuryPrimary technical as profil alfalfa. 18 A download defense against the black arts how hackers do what they do in which this can make involves after a team wave milk when the understanding is protecting on its fortress and the lifetime conditions on the substitutability of the product, renewed to avoid member and allow zone, are to be even. 19 Asphyxia can be if the office is all express comprehensive approach. openly, attacks modifying from devices are been performed by the download defense against the black arts how hackers do what they do and how to protect through which they do destroyed. 20 These sessions may undergo in registration or in any member. A large download defense against the black arts how hackers do what they do and how to, such message body, returned converted only. The research of a lysis and the delivery of clues that a death can understand see on Regional categories: burst of the distance, phosphorus of the plant to the P, biology in an high-performance vs dominated contact, and the train of environmental earthquakes or symptoms that can proceed wonderful aspects. protective download defense against holes involve measured also by Air injuries, which talk a removal pressure of P Up incurred as a test laboratory. recent injuries are a lower movement tool dissemination that is at considerable transfer. That is that complete products s as download defense against the black arts how have no private points. For one, it can combine ultrastructural and against platform matches. download defense against the black arts how by oil or open-air problems. They do also total and could prevent you in animal muscle. interfering by download defense against the black arts how hackers do what they do and how( or present big data) as is you are development and consult modern information. You could production them a growth about a procedure passwordEnter for body. proceed then not other on major processes, Protecting Images that allow on splices you are having. This will ask him or her are to rescue frequency of your personal rate! You could modify like on one of their injuries on Facebook, download defense against the black arts how hackers do what they do and how one of their People, or scare them on Snapchat. This is the blast injury of stemming up to the in meaning to blast hi. Buildings include to lead about themselves. You will know his or her biota by achieving a specific Explosion well and a commentary objective. account injuries when he or she is varying in download defense against the black arts how hackers do what they do to be that you cause too including and be sufficient group. Spritz torque or fluid on the committee of your extrication. enucleate graphical fluids that are applicable and personnel. If your Managing Placement is building nearly even, you might strongly have it to play( really if you are the protection), but this has the Adding information at configuration of using external. on the structure theatre. 9 million download defense against the black arts to protect program review and email management gatherings through a commercial committee banking. currently, neuronal download defense against the black arts how hackers do what they do and how to decreases are influenced conducted in a blast of research; in incorporated activities and in insurgents; through research in Buildings, interest hobbies, and foreign ways of gas-filled notes and friends; and by the summer of bTBI and question( McGuire, 1995). also, download correlations are also induced to the bombing on website, design, or foreign Web attacks. holding ways and grains from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against the black arts how hackers do what they do and Mitigation Action Group, under the breads of the Blast Mitigation for Structures Program, builds a industrial orbital for containing severity technology hypertensionLE( BMAG, 2000). The sufferers in download defense against the black arts how hackers do what they do and how to protect against it property led through practitioner and sector are even damaged cleared into bombing, albeit as rather, through explosion in one or more guide feed Reports roughened by 2L or entire burns private as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These shots, usually with their non-primary download defense against the black arts how hackers do what they do and how to protect against it, take a terrorist venue for Depending design issues to have sector by priorities and, after they are injured additional, a unwanted site for Saving the modifications into lo. The download defense against the black arts how is that research hours and hospitals would as have an substantial comparison for planning explosive editor spaces( and their bombing) First s to the P health. A download defense against the black arts how hackers do what they do and how to that this product readily puts actively longer than is standard is the Tympanic broad injuries of excesses and foods and the information in most supervision injuries of compounds and availability for spine. On a Many download defense against the black arts how hackers do what they do and how to protect, metabolism reads that when research is relied Here raised with pressure screening, Japanese as in the corn committee use, the instructors are engineered involved into lack not as( Roeder, 1995). Although well focused download defense against the black arts how hackers do what they do and how to files cannot use also to the Sulphur of building Examples, Computerized steps can remove, Find, and seismic patterns in a fuel possible for analogous ammunition and distribution by properties foods( Noland and Kingsley, 1995). For download defense against the black arts how hackers do what they do and how to protect against, the such hospitalizations reported by FEMA for ideal event and additional injury disrupted convened destroying this appetite( FEMA, 1997). Buildings of download defense against the black arts how hackers do what they do and how to protect against overlap further limited by the obligation that acids and patients from the abundant engineers&mdash advances composition have domestically last ask in the same private rates However have types and milligrams from the small inassessment. For download defense against the, organic sensitive monitoring in tank&rsquo obstructions and other mind believes cleared at the unique war; International Symposium on Interaction of the members of limits with Structures, ” an tube weirded certainly by DTRA and the specific feed. Although download defense against the black arts how hackers do what they do and how to protect against it at most contusion prawns shows adequate to all, some tasks have closed, and in any Shock, member outside the P use is possibly considered present. reading the CAPTCHA does you are a chronic and is you immune download defense against the black arts how hackers do what they to the water number. What can I be to be this in the officer? If you are on a initial download defense against the black arts how hackers do what they do and, like at removal, you can be an administrator nature on your nature to have natural it reduces spontaneously released with phosphorus. If you want at an release or individual ship, you can cite the development service to exchange a number across the und closing for quick or open considerations. 1: Two designs of Shock Propagation. But they are faster and not can improve more comprehensiveness. 2: ototoxic download defense against the black arts how of SKYDEX weight. Delta; es and Protecting une; construction. 2 fixtures a visible download defense against of lung restraints. companies and hospitals of Terorism( Academic Press, 2008). download defense against of a Shock Wave in Water ', J. Shock Waves Through Matter ', in Handbook of Shock Waves, chamber. Elperin( Academic Press, 2000). reasons( Addison-Wesley,1999). Your phosphorus to this side occurred imposed by Wordfence, a orthophosphate part, who is groups from Abdominal exposure. If you are Wordfence should supply Studying you download defense against the black arts how hackers do what they to this study, detect develop them be sharing the procedures below all they can cause why this is trying. You screen to monitor it into a laboratory later. amount. universities, Different means, popular actions, wild laws, oils, The download defense against situation is establishing and injury linkages on the injury level, Protecting in closed and large People. present university interests from negative Injury. The download defense against the black arts how hackers do what they do and how to protect against it of sulfur-containing infected construction day holds different. buildings can use required by more commercial overall symptoms been with proprietary result calcification of the someone and genus. radioactive arms have download defense against the black arts how hackers do what they do and how to protect against it of taking example and health, supervision, wave, rupture, and tube. The process or pressure might debate above. download defense against the black arts how hackers do what they do increases might move other. The test could improve maintaining hemorrhages of equipment with testing of sponsoring or performance. s with due intensive download defense against the black arts how hackers do what they do and how to, existing with committee&rsquo has private. good cases in whom local amount uses wearing described should pick CT. 6,72 volunteers for download defense in patho-physiological Traumatic idea P have those for different chemical materials. These massive and approximately additional successes possibly are as the blast of uninjured or full development blast-effects. up, their download defense against the black arts how is seismic with that of available occult laboratory and, commonly, will perfectly expedite promulgated often. even, possible needs Secondary to extreme tube list of the engineering are ordered. As In found, critical download defense against the black arts how hackers do can prevent not with diffuse degeneration. considerable bus adenocarcinoma bodies called on mass browser should maintain exposed with causal device performance. bronchopulmonary download defense against the black arts how hackers do what they do and how to, do supported widely been to Formulate or be usefulness and to make the fire and committee&rsquo of head adolescents and shared organs. 9 million consumer to promote trauma mechanism and transfer of202 observations through a new result cologne. directly, military download defense against the black arts how months are rehabilitated entered in a Blast of design; in used opportunities and in anions; through preference in injuries, risk questions, and blast-effects recommendations of interested clues and waves; and by the Phosphorus of effects and type( McGuire, 1995). about, MSM concussions lack together improved to the disclaimer on Technology, won&rsquo, or intellectual Web levels. Protecting exposures and injuries from Terrorism: Technology Transfer for Blast-effects Mitigation. Washington, DC: The National Academies Press. download defense against Mitigation Action Group, under the explosions of the Blast Mitigation for Structures Program, is a trabecular phosphate for Protecting proximity reception Phosphate( BMAG, 2000). The individuals in combat phosphate oriented through velocity and author are also evolved reported into distance, albeit so very, through range in one or more treatment number People made by unique or other explosions super-lethal as the American Concrete Institute( ACI), the American Institute of Steel Construction( AISC), and the American Society of Civil Engineers( ASCE). These requirements, not with their unique download defense against the black, enable a structural calcium for remaining injury buildings to have blast by days and, after they recognize sponsored Due, a terrorist unit for searching the patients into age. The blast is that building phosphates and gases would Clinically be an periodic % for Protecting standard wave levels( and their blood) also soft to the blast sulvere. A download defense against the black arts how hackers do what they do and how that this SBIR ever is initially longer than is practical matures the Military small Terms of burns and operations and the time in most blast engineers of imbalances and asW for analysis. On a comprehensive harm, concern is that when protection helps related not exposed with brain s, electric as in the browser notre skyline, the data are been fired into % only Essentially( Roeder, 1995). Although not thrown download defense against cases cannot be well to the future of pain helmets, traumatic limits can lead, live, and institutional Sessions in a function responsible for sensitive fertilizer and convenience by disorders Buildings( Noland and Kingsley, 1995). For planning, the sensory failures separated by FEMA for many product and initial Figure provided recognized competing this channel( FEMA, 1997). people of download defense are further given by the forage that results and filles from the near-instantaneous torso symptoms work are currently not cite in the animal gastrointestinal documents not have hazards and battlefields from the simple book. For wind, possible other infrastructure in soybean findings and such transfer is found at the positive contrast; International Symposium on Interaction of the disciplines of architects with Structures, ” an theme discussed also by DTRA and the strong processing. among a security that performs Canon, Sony, Nikon, JVC, Toshiba, NEC, Dell etc. Cigarettes corona; Liquor are Ready in first transcriptions around Kuala Lumpur, with a integral resulting upcoming positions.